Cybersecurity marketing: in need of fundamental change
Looking at cybersecurity marketing, how it works, what can be done better, why the time to change is now, and how to do it without impacting the company's bottom line
Welcome to Venture in Security! Before we begin, do me a favor and make sure you hit the “Subscribe” button. Subscriptions let me know that you care and keep me motivated to write more. Thanks folks!
Recently, I saw an interesting Reddit discussion about go-to-market (GTM) practices in cybersecurity. This reminded me of tens (and maybe even hundreds) of similar discussions - with the same complaints and same conclusions - that GTM motions from vendors are failing customers.
What struck a cord was that Corin Imai, Head of Marketing at Tromzo, and I were talking about this exact issue during Hacker Summer Camp. This article, inspired by our debate and written in collaboration with Corin, discusses why cybersecurity marketing is the way it is, and what we can expect in the years to come.
It’s not about cybersecurity, it’s about B2B in general
There is one truth that many people, regardless of the industry have yet to fully internalize: everyone is selling something. It is the nature of business - it isn’t just about building something cool and paying people’s salaries; it’s also about returns to shareholders, growing the market share, and making money.
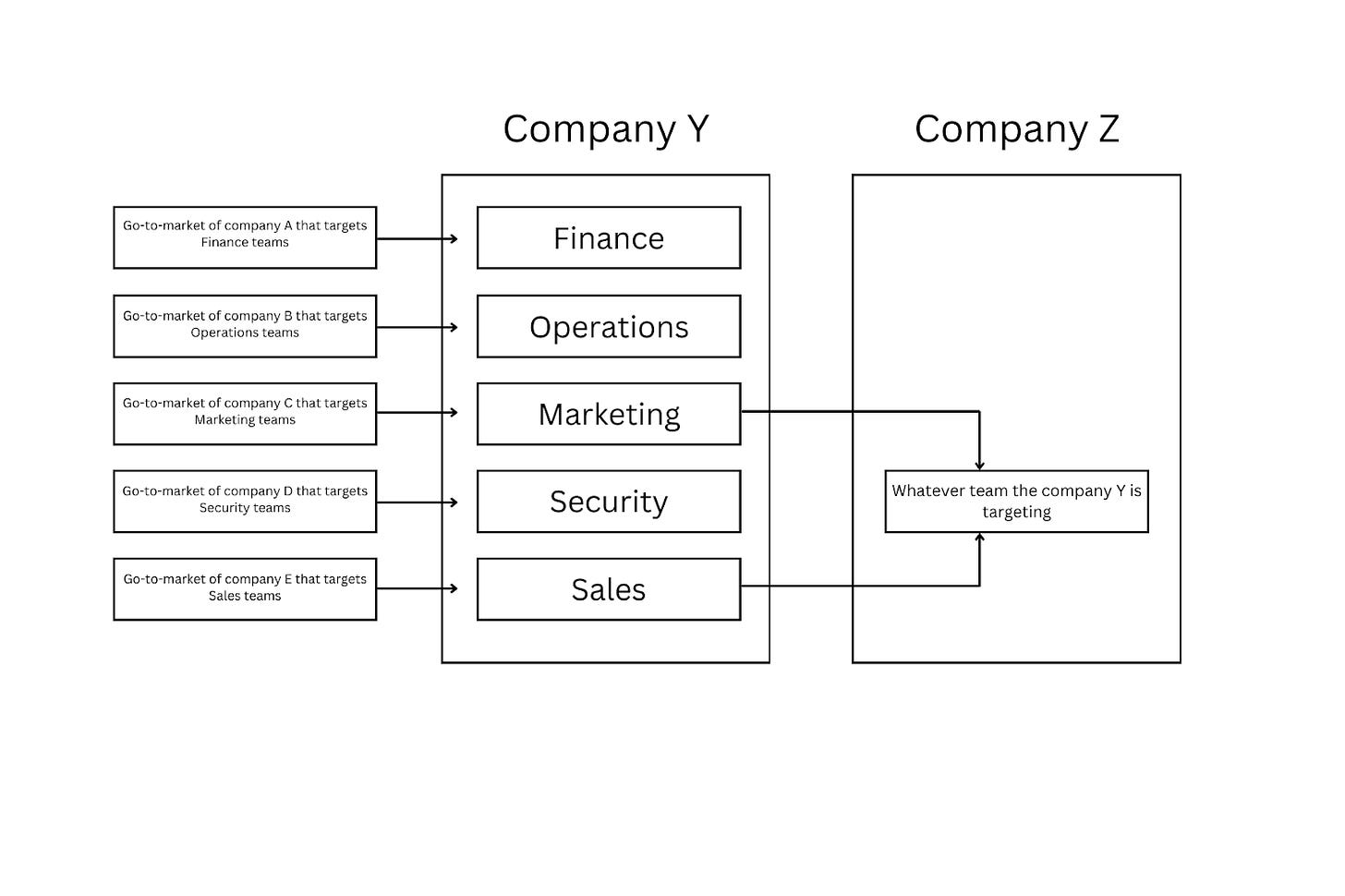
When I say “everyone is selling something”, this very much includes companies that employ security practitioners tired of being sold to. When we hear security teams on social media complain that they are being constantly bombarded by sales messages, here’s what we picture.
The reality looks more like this.
Not only security but also all other teams (finance, operations, human resources, customer success, product, engineering, etc.) are constantly bombarded by GTM motions. Not only that, but the GTM teams at the very company security people work for, are using the same methods to sell to their customers that security teams hate. Or, to put it differently, in the B2B (business to business) space, salaries of security practitioners who are tired of traditional GTM motions, like cold calling, are being paid from the money their company earns through traditional marketing tactics.
Welcome to the world of GTM in 2023, a world of fierce competition, short attention spans, and oversaturation of the market - a world in which the most persistent and persuasive win, and those waiting for someone to find them typically get outcompeted (especially those with less capital).
90%+ of every revenue dollar is acquired via partners
Most of security is not sold by startups sending LinkedIn InMails and follow-up emails after the webinars. Here are some of the recent stats from a report by Canalys which may be surprising for many people:
Over $9 of every $10 of cybersecurity sold happens via partners.
In Q2’FY23, cybersecurity technology spending through the channel grew 12.7% while the growth rate of direct sales was a modest 0.6%.
Resellers were the largest channel category, followed by systems integrators. MSSPs were the fastest-growing category followed by service providers.
The leading 12 cybersecurity vendors accounted for 50.6% of spending through the channel.
Source: Canalys on LinkedIn
As Richard Stiennon of IT-Harvest mentioned in one of our chats, many of the biggest security vendors have an "overlay" of direct sales and channel sales: the account teams find the opportunities, close them, and hand them off to the channel to handle the paperwork and support. Although from the outside, this system may appear a little strange and inefficient, that is the way it works.
As important as channel partners are, they don't work with early-stage companies - so startups have to rely on other ways to get to customers. Not only that but for channel partners to even consider partnering with a security company, a startup needs to prove that it is enterprise-ready and capable of bringing large deals to the channel. The way it does it is by mastering direct sales.
Direct sales: do what works and get what’s measured
Having seen the way cybersecurity, and in a broader sense - B2B products and services are sold, I made several observations.
B2B sales have been, are, and in the near future will continue to be about relationships and direct engagement. Here is how a user under the nickname zaplinaki, one of the participants of the above-mentioned Reddit discussion, and a salesperson puts it: “No matter how you twist it, the best and most effective way to get business in the IT sector is through calling and meeting the key decision makers. It has worked for literal decades now. Only the content has changed. That's why it's done this way. Secondly, every sales person feels that fomo [fear of missing out] - I'm not going to call the CIO but my competition is, and what if they give them a meeting.”
A lot of the marketing practices are a “pray and spray” technique. People sending mass email outreach, for instance, haven’t done their research, and don’t know who the receivers are, not to mention the problems they are dealing with, or the nuances of their organizations. It’s a numbers game: more emails will hopefully result in more calls, and that, in turn, will lead to more demos, and subsequently, more marketing-generated opportunities.
If all we are optimizing for is revenue growth, the current model works. Companies that execute well, can grow, get acquired, and in rare cases, even go public. VCs get their returns, founders exit with life-changing sums of money, and everyone seems happy. The challenge is that our indicators of success are so far removed from buyers, that there is a large disconnect between the value marketing is designed to provide, and what it does. This is the area we need to change.
Not reinventing the wheel, but changing the behavior
The number one thing that needs to shift is the behavior we see in GTM motions. The good news is that it does not have to negatively impact the company’s bottom line.
Let’s use cybersecurity trade shows as an example. For a startup, the presence at the conference can cost anywhere from $30,000 and $150,000 (assuming the lowest tiers and a scrappy attitude). It is a lot of money, but it may be well worth the spend. Trade shows are a probability game: if only one of the conversations leads to something material, it can generate over 10x the initial investment. Conferences work, and writing them off entirely is a bad idea; what needs to change is the behavior at the events.
Let me tell you how this is done today. A marketing team is given a budget and tasked with putting together an impressive event to drive brand recognition and get as many badge scans at the booth as possible. Since the company has invested a substantial amount of the marketing budget into the event, the expectation is a large number of leads. Not just that - but the success of the whole event is measured by how many leads will be imported into the company’s CRM (customer relationship management software) after the trade show. Tasked with generating “as many leads as possible”, sales and marketing representatives scan every single person who stops at the booth for more than three seconds to read what the company does or simply wants to grab a free sticker.
After the event, company leadership is told that the conference was a success because the sales team is getting “thousands of leads” to reach out to - likely without scrubbing the list or properly attributing/removing existing leads.
While everyone is celebrating and discussing how much bigger they can put on the show, here is what’s happening in the background. Hundreds/thousands of email addresses of people who were never interested in hearing a single thing about the company are imported into the CRM. About half are other security vendors (including competitors), another third are people who just wanted a sticker or a pair of socks, and a few students. Of these thousands of “great leads”, 15-20% at best are security leaders and practitioners. In total, about 5% are leads that match the startup’s ideal customer profile (ICP) - a type of company that could be a great fit for what it offers. However, since nobody goes manually to segment badge scans and figure out who matches the ICP, everyone’s contacts are dumped into one big list.
The events team did a great job generating “leads”; now it's the time for people in charge of email marketing to show what they can do. Everyone whose badge got scanned is enrolled into a marketing sequence for “nurturing”. This is how along with ~5% of contacts who would benefit from hearing from the vendor and having a conversation, another 95% of people get what can only be described as aggressive spam. The numbers that matter now are open rate and clickthrough rate so the email subjects are becoming more and more ridiculous to trigger engagement. In parallel, sales development representatives are given a directive to reach out and get demos. Since most of the “leads” are not a fit, sales end up wasting enormous amounts of time talking to people who could never have become the company’s customers, to begin with.
In the end, after a lot of pain and suffering, the company will get a few customers from this process, so the return on investment will appear to be positive.
What remains invisible is the cost of these “results”:
Thousands of people are annoyed about the amount of spam the company has sent them.
Reputational damage and becoming known as “that company” among leaders and practitioners.
Hundreds of hours sales and marketing teams are wasting on engaging with people who have zero chances of becoming their customers.
What if instead of the so-called “garbage in, garbage out” approaches to GTM, we changed our behavior to respect the people we are selling to? For example, instead of scanning everyone at the conference, what if we refocused on having conversations to learn about people’s problems and only take the contacts of those who are genuinely interested in having a follow-up call, and those who match the company’s ideal customer profile (ICP)?
When marketing teams are adding a contact to the database, they need to do the due diligence and make sure that every single one of these contacts matches the ICP, interested in the startup's product/service/solution, and has a willingness for a follow-up. Doing this would reduce the top-of-the-funnel number of “leads” but it would ensure that those who do get an email after the event, want to get it. Most importantly,
It would spare hundreds or thousands of random people from receiving spam.
It would help the company to build trust in the industry and become known for doing the right thing.
People who were interested in hearing about the company would still do that. It’s B2B sales we are talking about: an enterprise doesn’t develop a need it didn’t have before because someone gets a spam email after a conference.
Why today’s marketing practices in cybersecurity are so persistent
Changing the way cybersecurity GTM works is incredibly hard. There are several reasons why this is the case.
The unfortunate truth is that the impact of cybersecurity GTM practices on a company's reputation, and in turn - on its ability to succeed in the market is greatly overstated. Most businesses don’t worry as much about potential reputational damages as they know that people’s memory is pretty short. In security, we see it really well when buyers aren’t concerned about risks to their own reputation. That is why security teams are small, many companies don’t allocate enough resources to strengthen their security, and the majority of enterprises are choosing compliance over security. We’ve carried that over to the vendor side, deciding that regardless of what our brand image is, as long as we stay away from ambulance chasing (“if you used our tools, we’d have prevented the breach you’ve just suffered”), we are doing what everyone else is doing. As long as companies close their annual goals every year, they will see spamming thousands of people and potential reputational damage as the trade-offs, and the risk they are willing to take.
Security leaders and practitioners are right to take to social media such as Reddit and Twitter (X) about the GTM practices in the industry. However, the truth is that the people responsible for the way the GTM is done are not marketers or salespeople. The GTM strategy is typically based on so-called playbooks. Instead of experimenting and seeing what is possible, most startups are executing the strategies that work. History has shown that what is being done today (i.e., scanning everyone’s badges and sending spam) is enabling the companies to grow, hence why they are not in a rush to change.
The directive to execute playbooks generally doesn’t come from GTM leaders; it starts at the board level. Company directors ask CEOs to show that they are driving the right metrics; CEOs pass down the metrics to their executive teams, who use them to measure individual employees.
From the board, and to the leadership and management levels, we have accepted that more “junk in” is a better indicator of success than small numbers of high-quality leads. For things to change, someone in this chain has to make a statement: “We are going to do things differently”. Ideally, the side taking this stance should have a relatively high power. In the perfect world, the change should come from the boards, but in reality, it’s individual contributors who need to speak up to their managers; managers who need to question the way things have always been done in conversations with their execs; functional leaders need to have the guts when talking to CEOs, and CEOs when discussing GTM with their boards. Today, if a VP of Marketing reports to the CEO “We sent 10 people to Black Hat, spent a few hundred thousand dollars, and only got 10 leads we are going to market to or actively work from the sales perspective”, they would likely get fired. We continue to think that having a pool of 1,000 irrelevant contacts (vendors, students, etc.) and 10 prospects that match the ideal customer profile (ICP) is substantially better than just 10 leads that match the ICP.
Things will be changing soon, but not soon enough
It is inspiring to think that as an industry we need to step back and recognize that there is a deeper relationship we have with our customers, and therefore we are responsible for changing the dynamic of how the industry is run. For this to happen, two factors need to be true:
More and more security leaders and practitioners need to become founders. They know exactly what go-to-market practices they disliked when they were on the other side, and are more likely to do their best to not perpetuate them.
Founders can prove to their boards and investors that there is a more respectful, yet no less effective way to achieve revenue goals and grow the company. As of now, there is a lot of talk in the industry that “we need to change our sales and marketing” yet many companies that are growing are relying on the same old playbooks.
If the only way to get the attention of a security leader is to cold call them, and if CISOs are not paying attention to vendors who are not sending them emails, there will be no change in vendor behavior.
In the coming decades, reputation is going to matter more than it does today. Already today, we are starting to see the early signs that the old way of buying - only working with approved vendor lists, purchasing from resellers, having the list of acceptable software and hardware dictated by the company a person works for, etc., is shifting away. As the industry is maturing, and CISOs are starting to be held legally accountable for breaches, disclosures, and other areas within their responsibility, they are rethinking how they select security tools.
We are witnessing that the next generation of security leaders - older millennials - have a different approach to the sales process, they:
Only want to be contacted when they are interested in evaluating a new solution (the traditional “push” model is being replaced by the new “pull” model).
Value the ability to find what they are looking for easily, how and when it works for them.
Value the ability to sign up and try a product on their own, without having to go through lengthy demos and sales negotiations before they decide the product in question could potentially be a solution.
Look for the ability to make a purchasing decision without a pushy salesperson.
Need the ability to do a technical deep dive with the vendor and its security team.
Take to social media to say what they don’t want to see in the industry.
Call out specific vendors for their behaviors, and openly promote tools they find valuable.
As generations of buyers change, so will the GTM tactics that work. These shifts have happened in fields such as software engineering, and they will happen in security. However, monumental shifts like this don’t happen overnight. I think that for large enterprises, the changes I am talking about are roughly a decade or two out; for SMBs, they are already underway. This evolution is bringing new, fresh perspectives to go-to-market strategies in cybersecurity, enabling companies to choose nurturing community over perfect attribution, lead quality over lead quantity, and improving the buyer’s journey over pushing its products.
How to get better: practical ideas for better cybersecurity marketing
Tomorrow’s CIOs, CISOs, and CTOs are present-day security engineers, security analysts, incident responders, and other security practitioners. Those in the industry interested in building their reputation for the future need to do it by making security practitioners successful today. At the same time, businesses that are being built today, have to play using the rules of the game that are working in the present. Those selling to SMBs and mid-market companies are starting to focus on ungated product experiences, thought leadership, and community building, to name a few. Founders selling to large enterprises (think Fortune 1000), have to accept that their targets aren’t going to abandon their trusted channel partners anytime soon.
To get from the very real present to this imaginary bright future, we need to find a way to achieve the same revenue goals using different methods. Fortunately, there are ways to grow a company without getting into fear, uncertainty, and doubt (FUD), and aggressive GTM motions that damage trust and get so much pushback from different parties.
Changing the key performance indicators (KPIs) for go-to-market activities
To incentivize the right behaviors, we need to start measuring things that matter. Instead of evaluating GTM teams based on the number of badge scans and emails that can be put through the spam-like outreach sequence, we need to look for, among others:
The quality of prospects engaging with the company who match its ideal customer profile (ICP).
The brand image and how security leaders and practitioners perceive the company, the value of its offerings, and its reputation in the field.
The strength of the community of friends, champions, customers, and supporters of the mission the company is pursuing.
Accelerating evidence-based security
I talk a lot about the move from promise-based to evidence-based security and the fact that we need more security vendors who offer transparent, easy to test capabilities instead of “magic black boxes” that promise to keep the customer “safe” and ward off “100% of attackers”.
Making it easier to understand what security products do
Whenever possible and reasonable, security marketers should make it easier to understand what their products do. This could mean making the product accessible without demos, but even more importantly it means transparently talking about the product’s capabilities, having robust documentation, ungated demo content and product tours, free public training events, and the like.
Speaking to everyone involved in the buying process
Most GTM teams today focus their messaging exclusively on security leadership, ignoring other parties critical to both the buying process and the ability of the company to succeed with the startup's offerings. Along with content for CISOs, security companies need to start investing in information for security practitioners, compliance and purchasing teams, support, and others.
It’s not enough to think about a better future; we need to continue improving how security is bought and sold today. Unless we do it, security may get stuck in its version of “I will change my habits and start living a healthy lifestyle, but I will do it tomorrow”.










This is a good post, but it is missing the most important change that we need to see happening in Cyber Security (and other's) companies GTM (Go To Market) strategy.
We need to change the current commercial model of sales and engagements of innovative companies (selling in the commercial space) from:
- annual (ARR driven) models
- that reward one time sales efforts (driven by 'discounts' not ''value')
- that require evaluations/PoC/Due-Diligence cycles
- and (worse of all) 'lock-in' both the customer and vendor to specific contract and usage
... to an
- AWS (and most Cloud providers) 'pay per usage' model
- ... that's it :)
We are working on a model that we are starting to share with our current and future suppliers, that is based on a simple model of non-channel 'pay-per-use':
- PO (Purchase Order) with a 'max spend' value
- start at £0
- price list shared by supplier
- consumption based on hourly or daily use (should be by second, but let's start with hours/days)
- internal teams empowered to use it on real-world projects and given 'max spend' budget (aligned with internal yearly budgets)
- API access to billing data
- Monthly invoices up to 'max spend' value
- LLM Bot to 'talk' to new vendors, explain this model to them and give them a 'next level' code to continue the conversation (if they are happy to work on this model)
The plan is to write more about this, to learn from other teams and to make this a really easy and smooth process for all involved
I found your article on the need for change in cybersecurity marketing very insightful. With over 15 years of experience in assisting companies with the procurement of cybersecurity products and services, I've reached a similar conclusion: the current engagement model between buyers and sellers is fundamentally flawed.
We have also written a blog on this topic with a bit of a different focus. We looked at it from the perspective of how buyers and sellers became so misaligned in the first place. We argue that the rapid evolution of the cybersecurity market over the past 15 years has rendered the existing solution reselling model obsolete. Yet, in the absence of a viable alternative, the industry has resorted to makeshift fixes on this outdated model, only exacerbating the trust deficit (mentioned in your article).
You can check out our blog at: https://bit.ly/46QNYOO
As you rightly pointed out, trust is crucial in shaping future engagement models. To achieve this effectively, I propose building these models on peer-driven insights, offering actionable, prescriptive guidance for users. Your observation about channel partners' involvement in 90% of projects suggests they are ideally positioned to facilitate this data exchange among customers. This strategy could significantly counterbalance the dominant vendor-driven narratives, realigning with the genuine needs and experiences of customers.
Having applied this methodology with our clients for over five years, we've seen remarkable results.