Cybersecurity has a communication problem
It’s not that founders or CISOs are trying to be difficult, it’s that cybersecurity has a communication problem
If you ask most CISOs what they think of how security companies talk about what they do, they’ll tell you that startups are absolutely terrible at communication (and they’d be right). But, if you flip the question and ask others what it’s like working with security teams, you’ll hear a similar complaint, that security professionals and leaders are often just as bad at communicating with those around them. It’s not that founders or CISOs are trying to be difficult, it’s that cybersecurity has a communication problem. That’s what this piece is about.
This issue is brought to you by… Maze.
See What Really Matters: Maze’s AI Agents Triage Vulnerabilities for You
Security teams spend countless hours chasing vulnerabilities - most of which will never be exploited. A recent Maze case study on CVE‑2025‑27363 shows how our AI Agents investigate vulnerabilities like an expert human would to confirm if an issue is exploitable in your environment. If it’s irrelevant, it stays low priority. If it's actionable risk, it gets flagged fast.
That means less false positives, efficient remediation, and smarter security posture—without the usual guesswork.
Security is, among other things, a communication problem
When most people think about cybersecurity, they think about exploits, adversaries, threat intelligence, frameworks, and compliance standards, among many things. All this isn’t wrong, and security indeed comes with many layers and facets, all of which are very important. What I think gets forgotten is that, among many other things, security is fundamentally a communication problem.
Think this way: collectively, companies are spending billions of dollars every year, but most executives, boards, customers, and sometimes even security buyers struggle to understand what they’re getting for the money they’re spending. CISOs have to invest a lot of effort to get funding for important security initiatives because those who decide where budgets get allocated, oftentimes, simply don’t understand why they should care. On their part, security vendors are drowning in buzzwords and four-letter abbreviations, and buyers have no idea what value most companies offer (not necessarily because they aren’t valuable, but because they struggle to communicate that value). To make it worse, while every security person is used to seeing threats and attacks everywhere, most people outside of our industry are literally clueless about how big of a problem cybersecurity has become.
It’s important to be clear that all these problems aren’t due to the lack of trying. There is a growing number of PR and communication consultancies focused on helping security startups get their messages across, more and more CISOs and security professionals are vocal on social media, and even the general public gets exposed to more and more stories about security, through news, documentaries, and so on. Despite all this investment, we seem to be dealing with the same problems cyber has been dealing with a decade ago, and I’d argue a lot of that has to do with communication.
Communication failures across the cyber ecosystem
Cyber vendors lead with messaging that doesn’t land
Security vendors are notorious for a lack of clarity and for overcomplicating their value proposition. It is truly surprising how many companies can’t clearly answer basic questions, like what problem are you solving and for whom? Instead of getting to this clarity, founders and sales teams alike go into pitching specific features - AI agents, ML engines, behavior analytics, and similar, without grounding any of it in customer pain. All this makes many people in security say that “we have too many vendors” but as I’ve explained before, the problem isn’t that there are too many vendors, the problem is that most vendors all look alike because they can’t communicate what makes them different.
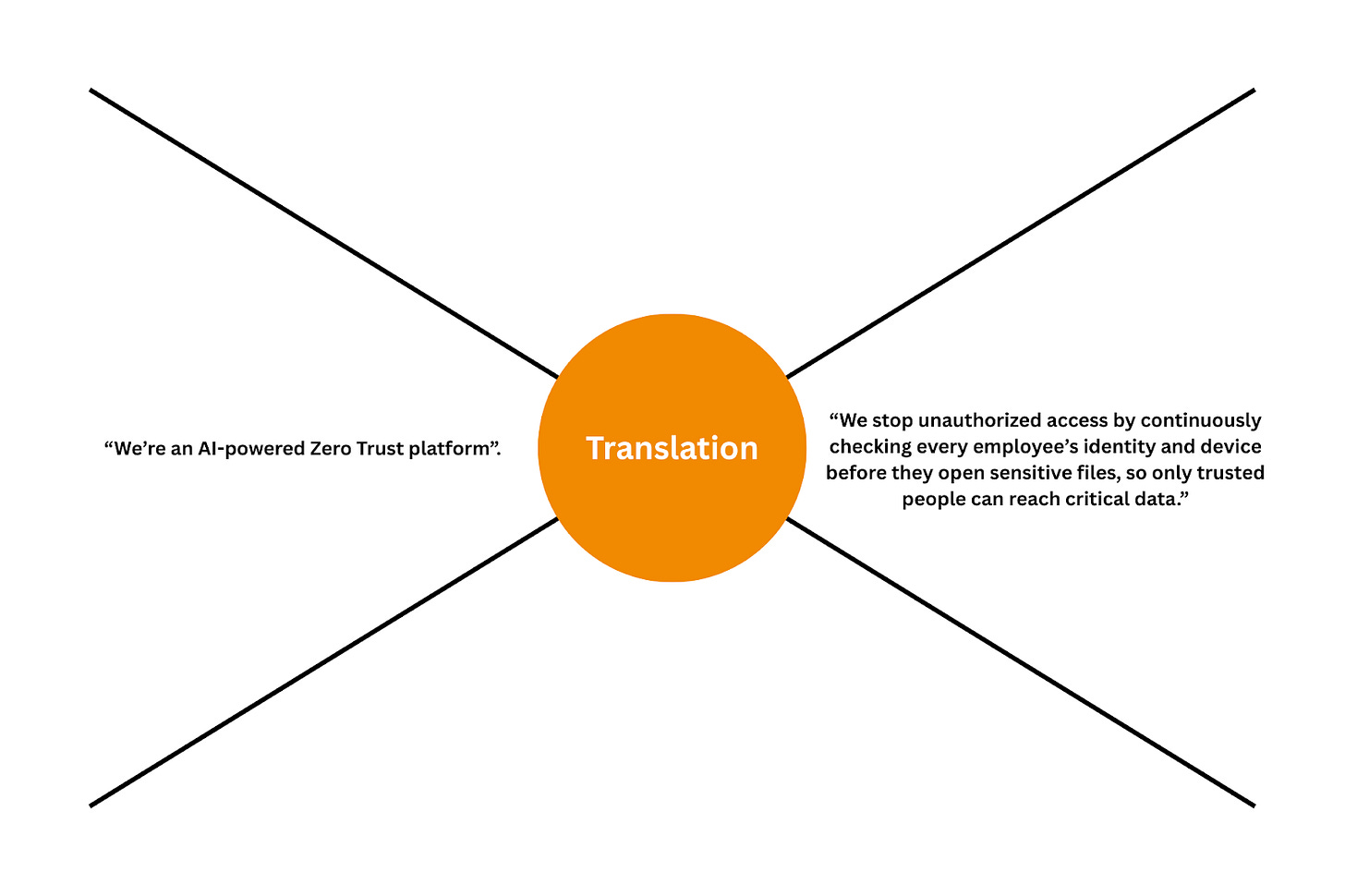
Buzzwords have become such a big part of cybersecurity that we no longer question them. Everything is “next-gen”, “AI-powered”, and “Zero Trust”, but most companies are unable to explain these terms in terms of outcomes. Now, let me be clear: the vast majority of the cybersecurity founders are passionate, driven, and honest people who get excited about solving real problems, and in many cases, the reason they struggle to convey what they are doing is communication problems.
Communication challenges often cost startups revenue and sometimes even make them fail. The way it happens is pretty simple: while vendors pitch how innovative their tech is, buyers are primarily looking to solve real operational challenges like reducing the number of alerts, securing cloud environments, enabling faster audits, or cutting down on manual work. When startups fail to map their value proposition to these problems, they can lose deals even if their products, in principle, would be able to solve customer problems.
What most security startups would probably describe as a marketing problem, I see as a communication problem. To solve it, founders need to develop clarity about what they are actually doing, for whom, what problems they are solving, and why the customers should care. I will be the first to admit that this is super hard, but I also think that it’s one of the most important problems early-stage startups need to figure out (everything else, like positioning, communication, and even product development, all start with this clarity).
Security practitioners struggle to translate risk into business language
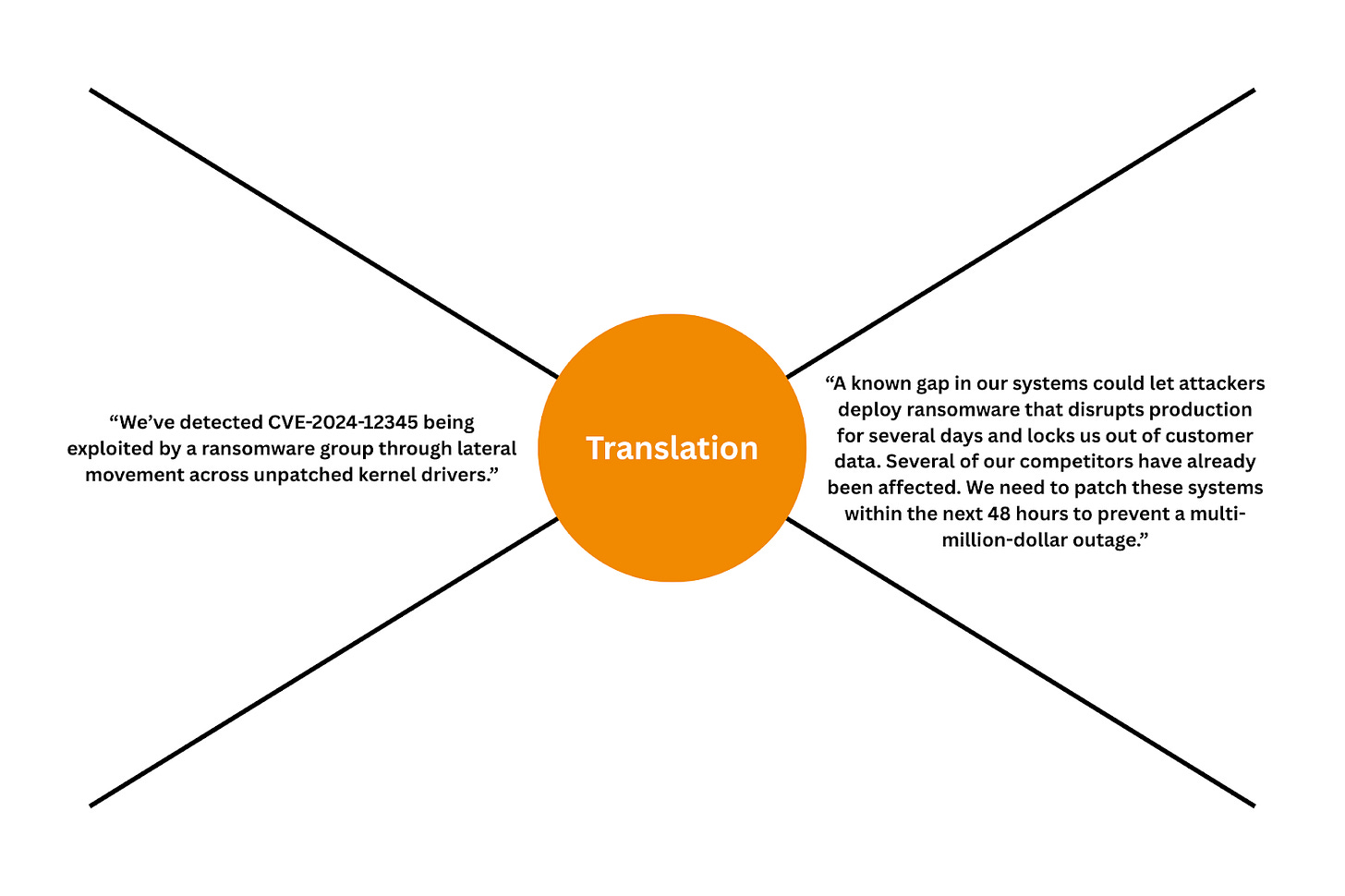
Security practitioners, for their part, also struggle with communication. They talk about threat actors, exploits, and lateral movement, concepts that make sense to other security people but sound like a foreign language to business leaders like the CFO or COO. Every technical profession has its own jargon, and that’s not just fine, it’s 100% expected. The question is, how do people in this profession communicate concepts to those who don’t have the same foundation?
Now and then, when I talk about this communication gap, some people tell me, “But why should security people be expected to adjust how they talk to business - why doesn’t business learn security?”. When I hear that, what comes to mind is how we talk to doctors. Medicine is complex, and every health issue has many complex medical terms. However, if we go to see the doctor, we expect that they will talk to us using simple words and not Latin terms. Another reason why I like this analogy is that in the past, doctors used to just tell patients what to do with no explanation (like prescribing security controls), but nowadays, patients are the ones who are being empowered to make decisions about their health, and the role of doctors is transforming into that of coaches and advisors. Doctors present options and communicate implications of different decisions, but patients decide what they want.
Business leaders care about how security risks can impact their revenue, customers, reputation, or operations. They care about outages, customer churn, regulatory fines, and competitive disadvantage, and not about which ransomware family is exploiting which kernel vulnerability. The disconnect here isn’t because those outside of security don’t care about details, but because many don’t see these details as relevant.
Regular employees don’t care about reducing risk; they care about doing their jobs without extra friction, complications, or fear of making mistakes. To resonate with them, security needs to be framed as something that allows them to do their work, not something that gets in the way. When people see security as supporting their success, not policing them, they’re far more likely to embrace it, and that too is at the core of security as a communication problem.
Security leaders struggle to get executive buy-in
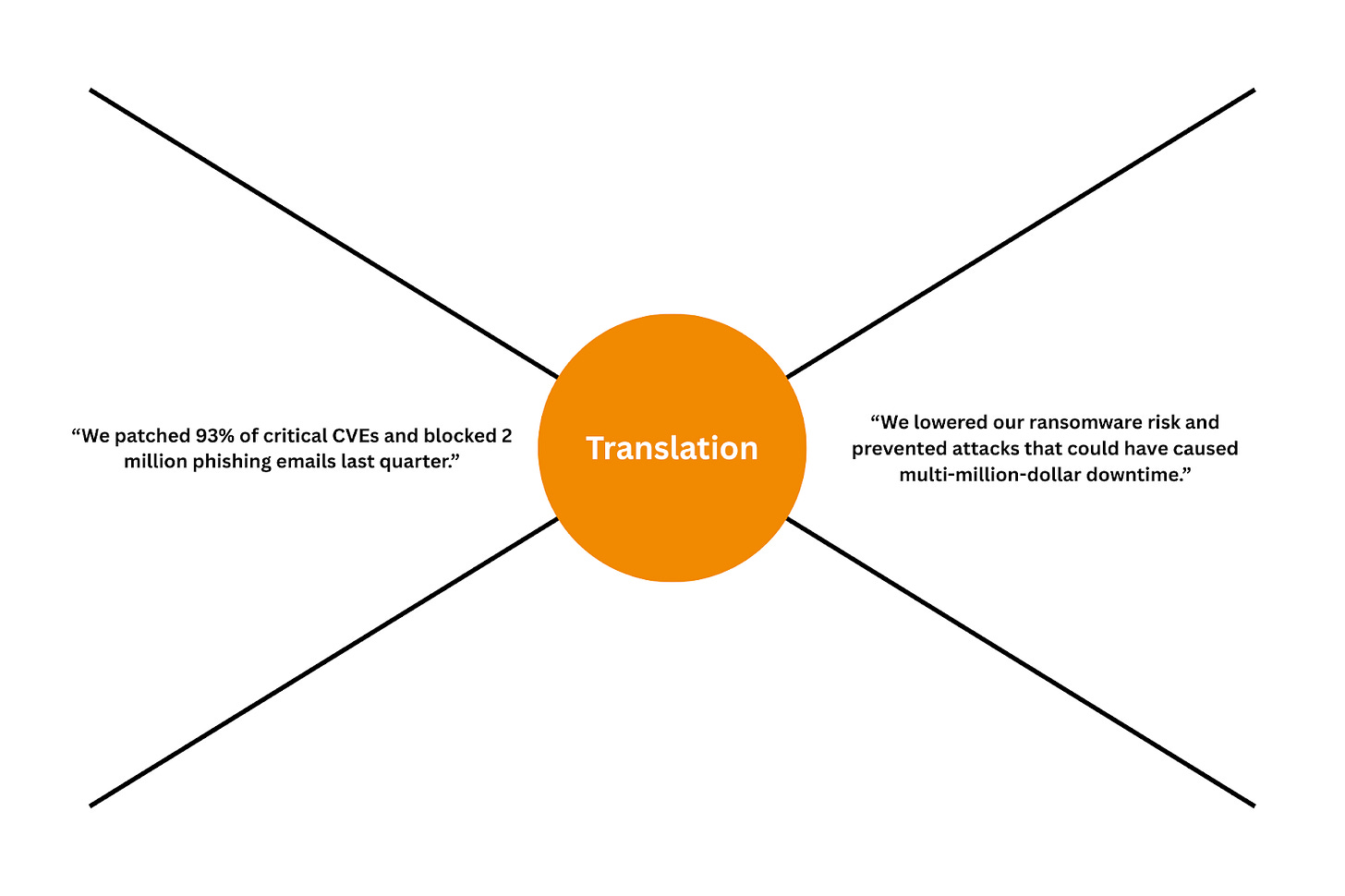
It’s not just security professionals but also security leaders who often struggle with communication. Oftentimes, the value of security is explained to the boards through the lenses of dashboards and reports generated by security tools, showing the number of blocked attacks, compliance scores, and other stats. This may work for some companies where boards are savvy enough to understand how these efforts translate into value for business, but for the majority, the links between company goals and security controls are less clear.
This misalignment is a direct result of the language barrier. Many CISOs speak in risk scores, vulnerabilities, and threat actors, while boards speak in terms of revenue, market share, and shareholder value. When directors don’t understand how security efforts translate into business outcomes, they become skeptical and disengaged. Leaders can’t support what they don’t understand, and they won’t invest in what they don’t trust.
There has been a lot of effort in the past several years to help security leaders become stronger board-level executives, and I think it’d be disrespectful to suggest stuff like “security leaders should frame their work in business terms”. Everyone knows that, and I haven’t met a single CISO in my career who would find this generic “advice” useful. The hard part is actually getting people to pay attention to something like security, and that requires both mastery beyond basics and a lot of relationship-building.
We as an industry are bad at communicating about risk with the public
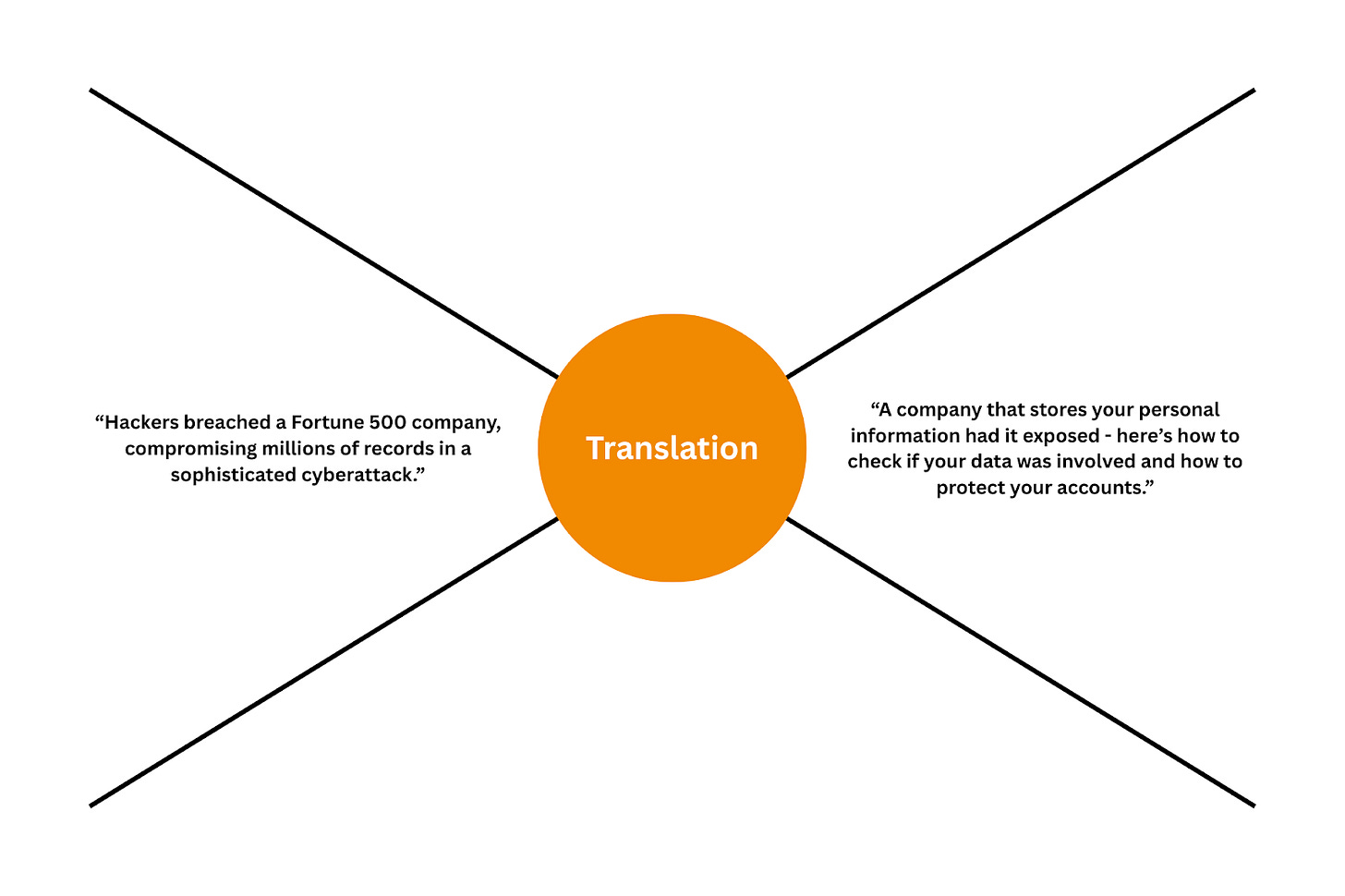
The cybersecurity communication problem extends beyond organizations to society at large. When regular people hear about security, it’s generally presented as an abstract threat - hackers in hoodies, invisible breaches, and “cyberwar on the horizon”. The news that some big corporations get breached doesn’t get people as upset as many would think, even though oftentimes it’s the data of these very people that gets compromised.
It’s a fact that an average person doesn’t understand cybersecurity. People read the news and are usually left either fearful or apathetic, unsure what any of it has to do with their daily lives. I have previously explained that people are really bad at understanding and managing risk. An infographic by the American National Safety Council does a great job illustrating that Americans often worry about the wrong things. For example, it highlights that:
The odds of dying when riding a car are substantially higher (1 in 470) compared to the odds of dying from a lightning strike (1 in 164,968).
The odds of being killed unintentionally are substantially higher (1 in 31) compared to the odds of being assaulted with a firearm (1 in 358).
The odds of being killed while walking down or crossing the street are substantially higher (1 in 704) compared to the odds of being stung by a bee, hornet, or wasp (1 in 55,764).
With security, a big problem is that people have no idea what to expect. Cyndi and Ron Gula at Gula Tech Adventures believe that one of the obstacles that keeps people from grasping the importance of cybersecurity is the way we talk about it (see, communication again). The word “cybersecurity” itself has too many aspects and flavors, and depending on who is using it and in what context, it may mean different things. The Gula Tech team wants to see the word “cybersecurity” replaced with “data care,” which would, in their opinion, make it a lot easier to communicate the personal responsibility every individual has to protect their data, and discuss with boards the risks to the company data. The word “security” in some cases can actually be a turn-off to minorities - think about policing, security monitoring, and the like, which have negative connotations with certain communities. “Data care” is neutral and easily understood by anyone.
The concept of data care is simple: we need to get people and organizations to take responsibility for the care of their data since data is what we want to have confidentiality, integrity, and availability of. Data care is similar to healthcare. Whenever someone is in pain, they should go see a doctor. We know that there are many specialists - cardiologists, immunologists, dermatologists, endocrinologists, and the like, but the average person would see a family doctor who would assess the problem and send them to the right care professional. Most importantly, we understand that while doctors are there to help when we are sick, it is our responsibility to take care of our diet, sleep, exercise, and other aspects that impact our well-being. What happens often in cybersecurity is that we are trying to make everyone a brain surgeon, or their cybersecurity equivalent - a security engineer, expecting an average person to become deeply proficient in security. That is, obviously, unrealistic, and instead of expecting that in five years, we can turn all kids and adults into Kevin Mandia, we need to teach them to take care of their own data. We can’t do that without changing the way we communicate.
Clarity and storytelling for cybersecurity
Communication is a very broad and all-encompassing skill, and saying that people in security need to improve their communication skills is just way too generic. That said, I think there are two aspects of communication that, if mastered, can truly change the trajectory of careers and the destiny of companies. I am talking about clarity and the art of storytelling.
Clarity is a prerequisite for effective communication. When I am talking about clarity, I mean being clear on what the person or the company is trying to communicate, to whom, and why they should care. Clarity is when people have a single, specific message that they want to get across, and a specific group of people they are trying to talk to. In cyber, it often feels to me like most company websites are about everything and the kitchen sink, and while they have many words, they don’t really come with a specific message.
While clarity is a prerequisite for effective communication, what makes communication successful is the art of storytelling. As an industry, we are used to relying on statistics, acronyms, and technical jargon to get our points across. The problem is, numbers and logic don’t move people. Humans make sense of the world through stories. They remember narratives, not dashboards, and they start to care when something feels personal, not when someone in a suit talks about some abstract probabilities or risk quantification (I am sorry to my friends doing this obviously important work). It’s not that math isn’t critical (it is!), it is just that it on its own doesn’t convince people - it has to be the foundation for storytelling.
It’s the stories that make risk real. Telling the board that the organization has a “3% phishing click rate” doesn’t create urgency, but telling them about an employee who clicked a fake invoice, how attackers almost got access to the company’s financial systems, and how close the business came to losing millions makes the risk tangible. Stories connect technical and non-technical worlds, they are like a universal language that can be understood by someone who is deep into the latest zero days, exploits, and attack paths, but also someone who doesn’t know what a zero day even means.
Most importantly, stories create emotional connection, and it’s this emotion that drives action. People protect what they care about, and they care about what they feel. A strong story makes security personal because it makes it something people can understand and relate to - their work, their data, their customers, their reputations. That’s why I think that one of the ways in which we can evolve security is by learning to tell better stories that make people listen, remember, and act.


I usually say, "Cybersecurity does not happen in the implementation; it happens in the conversation". We need to understand that conversation is the unit of communication. If we create better conversations, we may have better cybersecurity. At the end is an environment of trust that we create, not cybersecurity
Business leaders care about how security risks can impact their revenue, customers, reputation, or operations. They care about outages, customer churn, regulatory fines, and competitive disadvantage, and not about which ransomware family is exploiting which kernel vulnerability. The disconnect here isn’t because those outside of security don’t care about details, but because many don’t see these details as relevant.
This is key right here. Translating security risks and benefits into business impact whether positive or negative is what speaks to the CEO, CFO and the board.