The dark side of the moon: demystifying cybersecurity business management for CISOs and security practitioners
Zooming in on the business side of doing security, what it means, why we as an industry have not been great at understanding the business, and what we ought to be doing to move our field forward
If you are a regular reader of Venture in Security, you know that I often discuss the business side of the industry. Usually, I look at it from the ecosystem perspective, explaining the role different entities play in the industry, how they are all connected, which incentives impact the present of security, and what trends are shaping its future. In this deep dive, I am taking a different perspective and zooming in on the business side of doing security, what it means, why we as an industry have not been great at understanding the business, and what we ought to be doing to move our field forward.
Welcome to Venture in Security! Before we begin, do me a favor and make sure you hit the “Subscribe” button. Subscriptions let me know that you care and keep me motivated to write more. Thanks folks!
Over 1,970 copies of my best selling book “Cyber for Builders: The Essential Guide to Building a Cybersecurity Startup” have been delivered by Amazon so far. This book is unique as it talks about building cybersecurity startups. It is intended for current and aspiring cybersecurity startup founders, security practitioners, marketing and sales teams, product managers, investors, software developers, industry analysts, and others who are building the future of cybersecurity or interested in learning how to do it.
Two ways we look at security: practice of security and business of security
Practice of security
When security leaders and practitioners talk about cybersecurity, they usually view it as a practice. In other words, the main question they are trying to answer is “How do I defend my organization from bad actors?”.
Over the past several decades, we’ve established many great avenues for discussing the practice of security, sharing our learnings, and advancing the field forward. There are now events such as DEF CON, Black Hat, BSides, and Gartner Risk Management Summits, to name a few, that bring together security practitioners to discuss new developments, share experiences, and level up in their craft. We have Information Sharing and Analysis Centers (ISACS) that facilitate knowledge-sharing between security leaders within different industry verticals, Cybersecurity and Infrastructure Security Agency (CISA) that has been doing important work to defend against today’s threats and build a more secure and resilient infrastructure for the future, and a wide variety other institutions and communities that help us improve our defenses.
There is a full understanding that security is complex and that we as an industry need to continue evolving and maturing our practices and approaches. The discourse about what to do and how to do it well is happening in private conversations, industry groups, newsletters, podcasts, events, and via other means. All this combined with the passion I see when I talk to security professionals gives me a lot of optimism that we will continue to get better.
Cybersecurity as a business
Looking at security as a practice is important, but not enough if one wants to understand the holistic picture and achieve greater impact. Aside from being a practice, cybersecurity is also a great business.
When looking at security from the business angle, one will quickly realize just how many different parties and stakeholder groups are out there. This includes startups, mature product vendors, investors, resellers, integrators, service providers, insurance companies, lobbyists, analyst firms, and more. Each of these groups has its interests, motivations, and incentive systems, and it’s the intersection of these interests and how they overlap with the needs of security buyers that create what we know as a security industry.
Fewer sources cover the business side of the cybersecurity industry compared to security as a practice. There is my blog, Venture in Security, there’s Cole Grolmus’s Strategy of Security, Mike Privette’s Return on Security, and a handful more, many of whom are founders or investors. I am purposefully not talking about industry analysts here as the vast majority of them cover different market categories rather than the industry as a whole from the meta-level. At the same time, despite this lack of information, I see a large number of people learn by doing. More and more security leaders and practitioners are starting to participate in shaping the future of security on the ecosystem level, be it through participating in angel syndicates such as VIS Angels, SVCI, or CCL, taking on advisory roles with VC firms, such as Team8 Village, YL Venture Advisors, Merlin Ventures Advisors, Foregepoint Capital Advisors, Glilot Capital Advisory Board, and the like, or by angel investing and working with startups directly. Although security as a business continues to be much less understood than security as a practice, this has been slowly changing.
The missing piece: cybersecurity business management
The one area of knowledge that has not been receiving the attention it deserves is the business side of security as a practice or cybersecurity business management.
The business side of cybersecurity is not just about “CISOs needing to learn the business their company is in”. Framing the gap that exists in the industry as “CISOs don’t understand the business” is not only overly simplistic and dismissive, but it also doesn’t reflect the real state of affairs. The overwhelming majority of CISOs aren’t lost and waiting for security vendors to save them and give them guidance about what they need to care about. Yet, it is not hard to notice that there is something important still missing. That something is the understanding that in the context of an organization, cybersecurity is similar to other functional domains, be it engineering, IT, marketing, or operations, and as such, it needs to be managed as an area of business.
While the concept of business management isn’t new and is well-understood in just about any other mature business domain, be it IT, engineering, or sales, the topic of cybersecurity business management doesn’t get the attention it deserves. Before we explore the potential reasons why this might be the case, let’s first define what cybersecurity business management is.
At the core, the job of security leaders is to identify, mitigate, and manage risks that threaten the business's ability to achieve its mission and deliver value to the shareholders. To make this possible, security leaders rely on people, processes, and technology. They need to hire the right people and build effective teams, select the right tooling that fits the organization’s needs, fine-tune that tooling to the unique customer’s environment, set up systems and processes to detect and respond to threats and establish procedures that would enable the company to quickly recover from security incidents without disrupting the business operations.
Most of the time when people talk about managing cybersecurity better, they talk about cybersecurity administration - tactical elements of compliance and risk ownership. This approach is quite limiting as managing the business of security is not about risk, compliance, or running annual and by-annual assessments. It’s not even about doing performance reviews (although that’s one of the aspects).
As a part of their work managing a security program and defending an organization, CISOs have to:
Plan investments in their security program, ensuring that they are tied to the most important business initiatives the company is pursuing.
Manage supplier relationships.
Manage procurement, negotiate contract terms and pricing, etc.
Manage initiatives, projects, and portfolios of work.
Manage resources and people.
Manage knowledge, including its accumulation and distribution.
Manage reporting and metrics related to their security program, assessing the effectiveness of security investments, and ensuring optimal allocation of resources to the right problem areas.
All these areas of responsibility fall under a broad category of cybersecurity business management. When we say that security leaders need to level up and become business leaders, what we mean is that CISOs are now expected to not only ensure that their organization is protected but also master their ability to manage security as an area of business. What follows is that in reality, CISOs have three, not two core responsibilities: identifying risks, mitigating risks, and managing the business of security.
Current state of cybersecurity business management
Ownership of cybersecurity business management
Whether or not security leaders acknowledge cybersecurity business management as a critical part of running a security program, this work needs to be done regardless. The way this problem is being solved in most organizations is through a progression of manual people-time:
It starts with CISOs trying to handle cybersecurity business management responsibilities on their own. The work is done by integrating reporting dashboards offered by different vendors, Excel spreadsheets, PowerPoint presentations, and ad-hoc artifacts produced to address requests from other executive leaders, most commonly Chief Financial Officers (CFOs) and Chief Information Officers (CIOs).
As the number of responsibilities on CISOs’ plates pile up, often making it impossible to pay attention to everything, security leaders with access to some resources are forced to delegate the vast majority of their business management responsibilities to the key people on their team - Senior Directors, VPs, or, rarely, a dedicated Chief of Staff. Those that don’t have the luxury of being able to hire someone they can rely on, are often looking for ways to distribute these responsibilities between mid-level managers or delegate other tasks to their team.
Over time, the key people burn out wrangling cybersecurity business management work on top of their other responsibilities. Assuming that the security organization can find more budget, the hot potato of cybersecurity business management will get passed down to dedicated project, program, or portfolio managers.
It’s worth highlighting that while some of cybersecurity business management work can be delegated to parties outside of the security team such as the vendor (VMO) and project management offices (PMO), the vast majority of these responsibilities have to remain under the oversight of security leaders. Moreover, CISOs at mid-market enterprises rarely have the ability to delegate cybersecurity business management work and are expected to juggle these responsibilities with everything else that’s already on their plate.
Problems with leaving cybersecurity business management on autopilot
Although the concept of cybersecurity business management may be relatively new, the problems it is trying to address aren’t. We cannot ignore the fact that consciously or unconsciously, we have been doing cybersecurity business management for a long time.
There is indeed an argument that the way things are done today is working because security leaders are overwhelmed with too much work, so pushing the business side of their function to the bottom of their priorities is all we can do. If a security leader needs to, for example, understand suppliers and negotiate prices, there are value-added resellers, or a Procurement Management Office (PMO) in the organization who can do that work for them.
Security leaders should most definitely be looking to delegate responsibilities and outsource areas they don’t have the time and resources to cover to other parties. It is, however, important that while doing so, they understand what they are delegating and to what extent, establish oversight, and gain visibility into what they are getting and what incentives are at play. The same is already the case with managed security service providers (MSSPs) and other partners: there is a level of governance and oversight that gets drawn for each of the vendors, clear areas of responsibility, regular reporting, budget planning, and service level agreements (SLAs), to name some.
If the business side of cybersecurity is not managed intentionally, it can result in a wide variety of negative consequences, including:
Overpayment for security products and services.
High vendor price variability between different buyers.
High percentage of annual product churn.
Underutilization of the existing security investments.
Inability to tailor the security coverage to the organization’s needs.
Issues justifying new and existing security investments.
Cybersecurity project, program, and portfolio management as a profession
There are plenty of examples of how some of cybersecurity business management responsibilities can be delegated to dedicated project, program, or portfolio managers. Here is how Carnival Corporation described the requirements for its Cybersecurity Portfolio Manager role the company successfully filled several months ago:
Source: LinkedIn
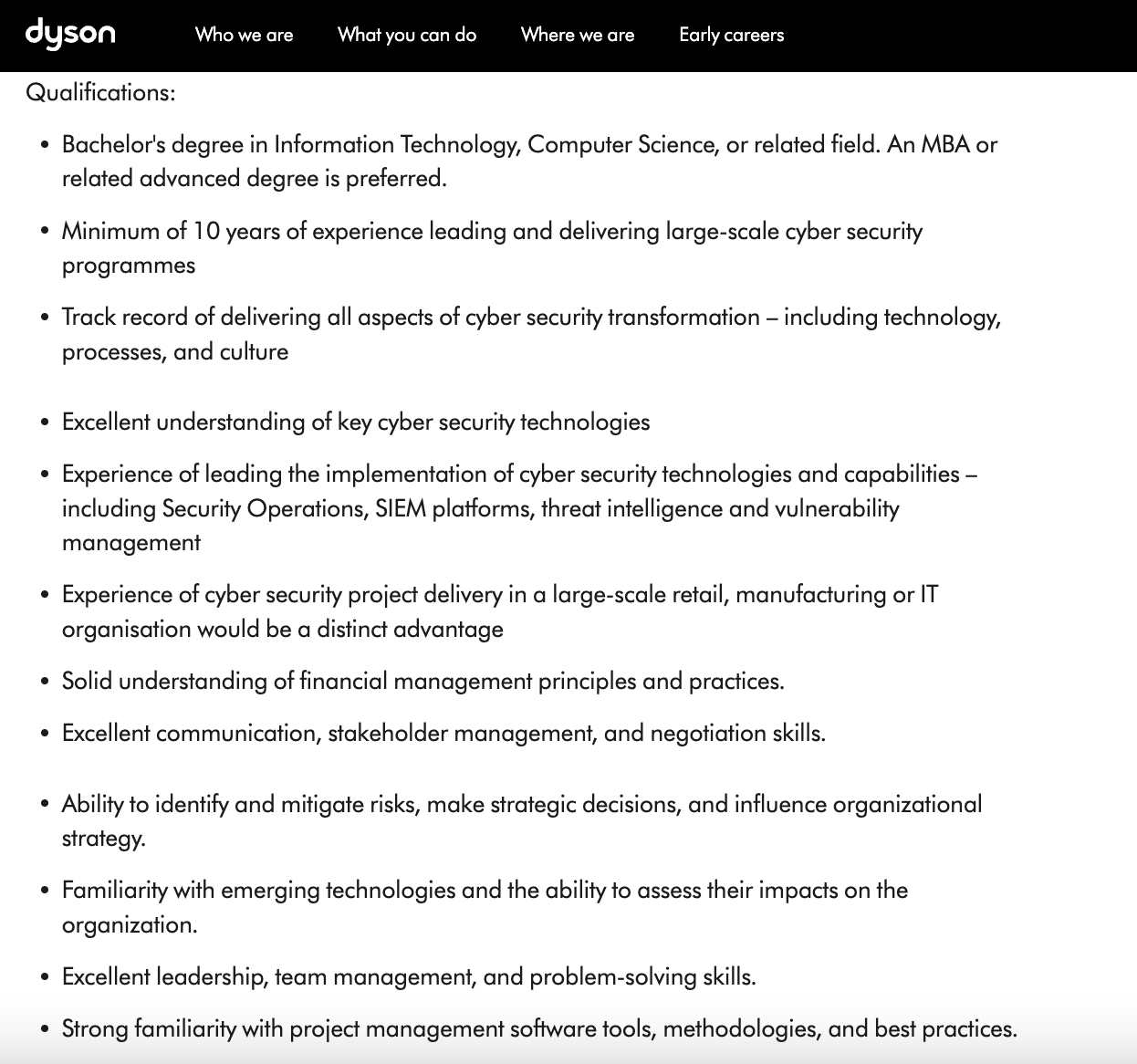
Dyson, one of the world’s leading manufacturers of household appliances which include vacuum cleaners, air purifiers, and hand dryers, as of 2022 employed just over 14,000 workers and generated a bit under $8.3 billion (£6.5 billion to be exact) in revenue. Here is how the company describes the role of a Cyber Security Portfolio Manager posted on its careers page in November 2023:
Here are the qualifications for the role:
As recently as at the end of 2023, Capital One was also looking for a Sr. Director - Cyber Portfolio Manager:
AbbVie, a pharmaceutical company employing over 50,000 people in 70+ countries, has also recently been looking for a Strategy Portfolio Manager, Information Security:
Source: Google
It is clear that although the business side of managing the practice of cybersecurity is not often discussed, we as an industry know how to articulate what we need and value people who possess the right skills and expertise. At the same time, it is also apparent that cybersecurity project, program, and portfolio management functions only exist at large enterprises and Fortune 1000 companies. Security leaders at small and medium-sized enterprises (between 100-500 employees and between $10M and $1B in annual revenue) are stretched too thin and expected to handle both securing their organizations and managing the business side of security without any additional help.
Why we don’t have a good level of maturity in cybersecurity business management
There are several reasons why as an industry, we are only beginning to discuss cybersecurity business management.
Security is a new area of the business
We know that cybersecurity as a profession is very recent. Having originated from phone phreaking and hacking circles, the field started to form as a professional discipline only after the emergence of the internet. Initially, security was one of the responsibilities of IT, and only in the past several decades, it has evolved into a separate business function.
Since for a long time, security was a function of IT, security professionals haven’t had the chance to develop a solid business acumen. IT took care of the business of technology, and security practitioners were asked to build technical security controls. In other words, IT leaders were responsible for IT, IT operations, and business of IT, while security people took care of the IT risk. For almost two decades, security practitioners weren’t in the room when the business of technology was discussed.
Today, security is no longer just a risk aspect of the IT department. It is now a separate area of business and as such, it is just starting to establish metrics, develop business management expertise, and get a voice in the room where the important business decisions are made.
The pace of changes in security is higher than in most other industries
The pace of changes in security is substantially higher than in most other industries. This is because it’s not just the competition and market demand but also highly motivated and well-resourced adversaries that are pushing the rate of innovation in the field. In practical terms, this means that for security teams, the research of new attack vectors and investments in new security tools is an ongoing challenge.
In areas such as IT, large initiatives are often followed by periods of maintenance. Say, after a company completes the majority of the work to move its infrastructure to the cloud, it starts to work in and mature a newly established ecosystem. In security, on the other hand, the vendor landscape changes more rapidly, and 50-80% of the tools security teams are using today might churn and be completely replaced 2-3 years later due to reasons such as consolidation, M&A activity, and a different threat landscape. To make matters worse, the ever-changing regulatory requirements make it highly unlikely that CISOs will get enough time to step back from firefighting and think about the bigger picture of running their department as a business function.
Security has lower budgets than IT
Depending on the organization, security budgets generally constitute between 5% and 15% of the IT budgets. As a consequence, IT leaders have more resources to hire people who can help with business administration, such as project, program, and portfolio managers. Security is hard to tie to revenue so hiring a management layer is not easy. Security leaders have little choice but to do their best, while fully understanding that something will naturally fall through the cracks.
Since CISOs’ main responsibility is to prevent and reduce the impact of security incidents, it is not surprising that it is the business side of their function that tends to suffer. It is worth highlighting that security isn’t the only “results-driven” function. One might argue that at the executive level, the same applies to just any business area. For example, while Chief Revenue Officers (CROs) are expected to manage the business of sales, it’s their ability to achieve revenue targets that will keep them on the job. What’s different about security is that to compensate for the lack of resources, CISOs have to get hands-on. CISOs spend their time researching the latest attack vectors, getting familiar with new product categories, and planning their security programs and resource requirements. When they are asked to reconcile their annual operating spending plan because the CFO wants to understand the investment areas and success criteria for each, most CISOs aren’t excited to have these conversations - not just because they aren’t interesting, but because they are already struggling to find time to just keep the department running.
Status quo works quite well for some parts of the industry
The fact that CISOs at large enterprises haven’t been able to prioritize management of security as a business function, works quite well for some large consulting firms.
The top consulting firms are used to building bespoke solutions for their clients instead of helping them develop internal proficiency and reduce reliance on third parties. It’s not uncommon to see one of the big four kick off three large engagements for a security enterprise, and then start a fourth one to connect the previous three. The fact that so many security organizations at large enterprises struggle with cybersecurity business management created a continued pipeline of new business for consulting firms eager to step in and offer a helping hand.
While the CISOs of large enterprises may have the resources to work with consulting firms, leverage tertiary business functions such as corporate project management office (PMO), or hire dedicated people who thrive in the business management side of cybersecurity, those in smaller organizations are less fortunate. They are forced to take care of the business management of security on their own. In practice, this means that they rarely get time and resources to look at their security investments holistically, and instead are stuck in firefighting mode just trying to get their under-resourced security programs running.
The need to mature cybersecurity business management
In 2024, security leaders are forced to navigate a long list of challenges, which include:
Defending their organizations from ever-growing threats in a rapidly changing environment.
Justifying increasing investments in security while other departments are cutting their expenses and focusing on achieving efficiencies.
Understanding and managing existing investments against new priorities.
Consolidating and rationalizing spending, reducing the number of vendors, and ensuring that all tools are being utilized to their fullest potential.
Responding to regulations and ensuring that the organization remains compliant with the growing list of requirements.
Getting buy-in from executive leaders and corporate boards for security initiatives.
While CISOs are struggling to keep their heads above the water, we continue to hear that “Security leaders need to be able to contribute on the board level”, “Security must become a business enabler”, and “CISOs need to level up and become business leaders”. Although these statements are repeated so often that we no longer treat them seriously, there are rarely, if ever, specific recommendations about what security leaders should be doing to get there.
Some industry conferences have in the past several years started adding CISO-focused tracks that discuss problems such as hiring, building teams, executive leadership, and board-level contributions. The latter, in particular, has received a lot of attention: although the SEC eventually rolled back the proposed requirements which would require annual reporting or certain proxy disclosure about the board of directors' cybersecurity expertise, it is clear that corporate boards need to have someone who understands security and risk management. In discussions about board-level security leadership, we often miss the fact that before becoming corporate business leaders, CISOs need to ensure they have full control over the business side of security.
Many of today’s security leaders are technical leaders first, and business leaders second. This has been changing and will continue to change as we go into the future. C-level executives, be it Chief Revenue Officer (CRO), Chief Technology Officer (CTO), Chief Human Resources Officer (CHRO), or Chief Information Security Officer (CISO), need to be able to show impact and alignment of the initiatives they are leading with the goals of the business.
The following are some of the areas we should be looking to drive to get cybersecurity business management to higher levels of maturity.
Creating opportunities for knowledge sharing
We need more conferences, talks, panel sessions, and discussions focused on the business of security. There is a lot we as an industry need to develop - from business metrics (maybe, there are better metrics for security than time to respond and cost per control), to best practices for security project and portfolio management, budget allocation, supplier negotiations, recruitment, team building, and building executive alignment.
Encouraging education about the business of security
We would greatly benefit from having more accessible executive education programs for current and aspiring security leaders. We must admit that as an industry, we’re lacking institutions and places where CISOs can learn about how to be good leaders without being sold. There are programs led by educational institutions such as Carnegie Mellon, NYU, Wharton, and Duke, but not all of them are equally practical or accessible to security leaders outside of Fortune 1000. Moreover, many professional development and peer leadership summits are sponsored by vendors that are trying to market their tools and build relationships. The CISO profession cannot evolve if security leaders aren’t able to find the time and resources to invest in growing their business leadership skills.
Going beyond adding more security tools
The 2023 Panaseer security leaders report states that most security breaches could have been prevented by the tools enterprises already have in place. This is in line with the deep dive I published before titled “Tools alone won't save us but if we have tools - why don't we at least use them?”. I think it’s important that security organizations do not mistake purchasing tools for running security programs. Instead, they must think about their security programs holistically and ensure that they know and prioritize the right programs. It is way too easy to get overwhelmed and flooded with too many findings that an organization simply doesn’t have the resources to prioritize.
Source: 2023 Panaseer security leaders report
Establishing tools and infrastructure for cybersecurity business management
We need to build tools and infrastructure that will make it easier for security leaders to manage cybersecurity as a business function. The good news is that we are starting to see some movement in this direction.
Balance Theory, a company where I am an advisor, offers CISOs the easy button for all business management functions, helping them to solve problems around budget pressure, investment justification, and business alignment. Balance Theory tracks over 3500 security vendors and 10k+ security products in the industry’s leading intelligence platform. In addition, the company offers a unified platform for complete management of the organization’s security investments and provides negotiation support to help CISOs get the best price and terms on their security purchases.
Reach Security and Enterprise Security Profiler, on the other hand, help security leaders and practitioners to measure, manage, and increase the value they're getting from their existing security investments. Reach Security, for instance, describes the problem it solves in simple terms: “Security teams work diligently on a daily basis to combat sophisticated threats that target the organization, but lack the time and resources to tailor their security products to the environment they’re defending”.
Another player that fits this context is SeeMetrics, a startup with a platform and solution for real-time and automated security performance management. The SeeMetrics platform helps security leaders to identify inefficiencies, from stack utilization to resource management, as well as see, track and improve operations. Vena Security, another relevant solution, is a defense optimization platform that analyzes threats, risks, and defenses holistically, enhancing security tool effectiveness and reducing threat exposure. And, Zafran’s risk & mitigation platform promises to “defuse threat exploitation by mobilizing existing security tools”.
Needless to say, these are just some examples and not a comprehensive list of tools focusing on the business side of cybersecurity. It’s worth emphasizing that tooling isn’t the main concern. With the right mindset, security leaders can, if they want to, adopt and integrate tools like ServiceNow, Confluence, Sharepoint, Excel spreadsheets, and countless vendor reports to their needs (it may not always be easy but it can be done).
Measuring return on security investments
In the past several years, more and more companies have been forced to push for efficiency and cut expenses in different areas of the business. As regulators are starting to look for ways to increase the bar for security, the CISO role has become more visible than ever before. At the same time, company executives and boards are starting to ask what they are paying for when they invest in security and what they’re getting for it.
Measuring return on security investments is hard. The same is true when it comes to measuring the impact of different technical controls. Many functional areas can connect the impact of their work to revenue, but not security. Is a company more secure with a SIEM than it was without a SIEM? How about SOAR? Similar to how security practitioners are finding it hard to evaluate different tooling, CISOs often struggle to communicate the impact of security investments to their counterparts in finance, operations, and IT.
Sometimes it feels like the best we can do is to evaluate security investment from the lenses of cost per control and time to respond. Although blending the cost and risk into some measurable unit may indeed be the obvious thing to do, I am not certain if there is not anything else we could be doing. As an industry, we need to continue looking for ways to measure return on security investments and have a discourse about approaches that could help security teams better communicate their value to the business.
Learning from other fields
We have no choice but to continue to mature cybersecurity business management. The good news is that we have the opportunity to learn from other verticals, such as IT, instead of reinventing the wheel and doing everything ourselves. We can shorten the amount of time it will take us to get a good grasp of the business side of security by talking to and learning from other executive leaders, including CIOs, CROs, CTOs, and CHROs.
Learning from other disciplines: IT business management
While we are still at the very early stages of understanding what cybersecurity business management is, other disciplines such as sales, marketing, and finance have accumulated a solid knowledge base about the business side of their functions.
Given that security generally follows the evolution of IT, it’s worth having a closer look at the area of IT business management.
In the 1970s and 1980s, as the field of IT was emerging into a separate discipline, businesses treated it as a support function designed to take care of “technical things”. Over time, as the complexity of IT grew, and the value of technology investments continued to increase, IT departments had to learn how to develop strategies, plan, manage, and ensure the success of large-scale, multi-million dollar initiatives. This need gave rise to knowledge areas such as IT Financial Management, Technology Expense Management, IT Portfolio Management, Strategic Portfolio Management, and ultimately, IT Business Management. Although each of them focuses on a unique set of aspects surrounding the management of IT, the problems they are trying to solve are similar:
Help align the technology investments with the business goals, strategies, and priorities.
Translate strategic goals into specific projects, and define clear objectives, milestones, and success criteria.
Help control how much time and resources are spent on different projects and reallocate resources or adjust project scope as priorities change.
Gain real-time visibility into the performance of the organization’s investments.
Enable organizations to stay flexible and pivot their strategies at a moment’s notice due to changes in the regulatory environment, business goals, etc.
Reduce the amount of time spent on administrative, non-value-added activities, minimize duplication, and shorten the amount of time needed to implement new initiatives.
Effectively identify and mitigate risks associated with IT initiatives.
Help break down silos and foster stronger relationships between business partners.
Here is how Deloitte, one of the big four consulting firms, thinks about the challenges faced by the IT function: “The technology function in many organizations is under siege:
New technologies are emerging and evolving quickly, which is a source of power as well as a source of disruption.
Talent pools are more varied and complex than former full-time equivalent (FTE) models. This offers flexibility, but it also adds to the management and planning challenge.
Stakeholders expect more, which is the traditional reward for past achievement, the natural expectation in the wake of rising investments, and a source of ever-mounting pressure to perform.
Traditionally, organizations measured the value of technology in tangible terms such as cost, control, simplification, reliability, and compliance.
Now, technology is increasingly called on to answer more complex expectations such as agility, fluency, transparency, and experience. Organizations want technology not only to monitor and preserve value but also to help create it.
This calls for a new approach to managing enterprise technology that’s responsive and aligns business and IT strategies.”
If we were to substitute “technology” for “security”, it becomes clear that the two disciplines share a lot of the same challenges. The same Deloitte web page goes on to explain the value-add of technology business management: “Technology business management helps solve their challenges with IT cost reduction strategies, return on investment, and the ability to turn transparency into agility. It can also show technology leaders how TBM helps make their contributions more visible and comprehensible—and elevates their work to the center of organizational strategy.
This means technology business management potentially offers both enterprise and personal benefits: It can help leaders save money, redeploy resources more effectively, gain respect, and secure tenure.
Dollars and cents. More visibility into where technology spending is going means more opportunities to eliminate waste, reallocate it to other technology needs, or apply it to other parts of the business.
A seat at the table. Technology leaders have more to offer in strategy and enterprise decision-making when they have a firmer grasp of their own operations. Both the people and the company can benefit when roles that were once order-takers can reemerge as trusted advisers.
Clear decision-making. The heart of technology’s value is the portfolio. When TBM illuminates the portfolio’s alignment to strategy, resource efficiency, adherence to finance goals, and risk status, the entire organization can benefit from faster, sharper decisions.
Leadership stability. When effective leaders are able to measure their tenures in decades, it’s good for them and for the organization. TBM helps promote long-term leader stability by boosting effectiveness and intra-organization cooperation.
Many of the tools and approaches that make up TBM are connected to enterprise technology. But they aren’t direct technology solutions. It’s important to understand that TBM is a business solution, not a technology solution.”
To address the needs of IT organizations, Deloitte offers help along six dimensions of technology business management:
Business outcome management.
Portfolio and financial management.
Demand management.
Product and solution delivery.
Services management.
Talent and partnerships management.
Source: Deloitte
Aside from accumulating a solid knowledge of business management, disciplines such as IT, sales, marketing, and finance are benefitting from well-established infrastructure to operationalize this knowledge. This includes:
Educational programs.
Software tools.
Industry conferences.
Here are some examples of solutions that unify management in different business verticals:
Closing thoughts: looking into the future
In the last two decades, we have witnessed how the focus on business management has reshaped a variety of markets. We’ve seen the rise of IT business management, sales management, marketing management, and the like. Marketing, for instance, is now looking at spend allocation, running, and A/B testing campaigns, while sales are tracking time to close, efficiency, and lead to opportunity conversion rates. Every business function is expected to show how it helps achieve the business goals, and how every dollar invested leads to measurable outcomes. It’s not a matter of if but when security is going to be expected to do the same.
Some times are good and CISOs can get budgets for whatever they need, be it best-of-breed tools or best-in-class senior security practitioners. However, when the economy is in recession, growth rates are slowing, the pace of change is compounding, and corporations are pushing for efficiency and cost-cutting across the board, becoming good at managing business becomes a necessity. It has become harder to run security programs than it was a year or two ago, and when the budgets are limited, CISOs have no choice but to become more resourceful. I think the economic conditions we see today are creating a perfect opportunity to start a discourse about what it means to manage security as a business function, and how we collectively can become good at doing it.
Today, nearly all of the security team’s time, people, and resources in most organizations are focused on the identification, mitigation, and management of risk, as well as firefighting during security incidents. A modest investment in the business side of security can enable CISOs to better understand what tools and resources they have at their disposal, what skills are available on their teams, where the opportunities for improvement may be, and how their investments are tied to the broader business goals. This, in turn, can lead to higher team productivity, cost savings, better deals with suppliers, and an ability to leverage more functionality of existing products instead of constantly introducing new tools to the company’s security stack. Most importantly, paying attention to the business of security will help CISOs evolve from functional leaders into business leaders - something we as an industry would greatly benefit from.











Fantastic piece Ross
Definitely a lot of useful discussion points here. Great work!