Why security teams should start recruiting product managers
Imagining how people with a product mindset and skillset would transform the cybersecurity industry
Welcome to Venture in Security! Before we begin, do me a favor and make sure you hit the “Subscribe” button. Subscriptions let me know that you care and keep me motivated to write more. Thanks folks!
Key Takeaways:
⭐ The goal of a product manager — a role that works with software engineers and designers in software development teams — is to make a product succeed.
🧑 Product managers work to uncover the user needs, prioritize what to build, rally the team around the product roadmap, help teams to deliver products and features, and champion the team so that everyone is motivated and empowered to excel.
⚒️ As security is getting more complex, we will need technical experts deeply specialized in their respective fields and focused on technology. At the same time, we will also need people to connect the dots across different stakeholder groups, while championing cybersecurity.
🚀 A PM-like Security Champion could do a lot of the critical, people-centered work including identifying what the company & the users need, prioritizing the security initiatives, rallying the team around security, and more.
The art and science of product management
What is product management? If you were to do some googling, it’s most likely that you would see definitions similar to the following:
The process of launching a product or service
The process of identifying the customer problems, needs, and goals, and designing a solution that addresses these
A way of advocating for customer needs and being a voice of the customer
The process of identifying the “why” behind the product and formulating the strategy to define how the product will solve a customer’s problem, how the product will reach the customer (the so-called “go-to-market”), how the customer can receive value from using the product, and how the company can receive value from providing the solution.
There are many different ways to define product management. I often think of it as a way to ensure the product’s overall success. It’s a broad definition, but precision is not the goal. It’s much more valuable to understand what a product manager does.
The role of a product manager
To succeed in this role, product managers are expected to excel in a broad range of areas. You can often see the Venn diagram to show an intersection between UX, business, and technology where a PM role supposedly resides.
This diagram illustrates the following:
To solve problems for the customer in a way that makes them more likely to benefit from the product, a product manager needs to be obsessed with the customer and their experience. While a PM is not expected to have a background in user experience (UX), it is helpful to understand the principles of human-centered design and be curious about how people use specific solutions.
To design feasible solutions and to understand technical constraints impacting the implementation, product managers need to understand technology. While a background in engineering is not a requirement unless a PM is working on a very technical product or a product built for engineers, it is expected that a product manager is capable of working with engineers and being able to discuss the trade-offs of specific technical solutions.
To ensure that the company is able to capture value, a product manager needs to be an expert on the company business. A PM is expected to be well-versed in the company business model, understand what decisions drive revenues, how different functional groups such as marketing, operations, sales, engineering, and customer success fit together, and be capable of ensuring that everyone who affects or can be affected by the product success is always up to speed and supportive of the product.
While this sounds like a lot, I did not even begin to describe what the product manager actually does. Dottie Schrock of ProductBoard did a great job organizing the responsibilities of a PM under five categories:
1.Discover what users need
The process of problem, product, and customer discovery is at the core of a PM’s responsibility. To fulfill it, a product manager reviews product feedback coming from different sources, conducts customer interviews and discovery sessions to better understand the problem, together with designers & developers brainstorms, prototypes, and validates potential solutions to confirm that they address the customer’s problem.
2. Prioritize what to build
Product managers are responsible to ensure that designers & engineers are always focused on the highest value items. To fulfill this responsibility, a PM conducts market & competitive analysis, stays up to speed with the industry trends, works with the company leadership to align product strategy with the overall product strategy, collaborates with finance, legal, operations, sales, marketing, and other functional groups to ensure their needs are met, works with the engineering team to ensure that planned features & solutions are feasible and achievable, and prioritizes the backlog, among other initiatives.
3. Rally the team around the roadmap
The success of modern tech businesses is synonymous with the success of their products, which is why product managers need to evangelize the product roadmap and rally the team around it. To fulfill this critical responsibility, product managers deliver presentations at the monthly or quarterly roadmap meetings as well as weekly all-hands, regularly communicate with marketing, sales, and customer support to ensure everyone has what they need to succeed when the new functionality is related, and work tirelessly to identify gaps and misalignments.
4. Deliver the feature
No matter how good the product manager is at planning and fostering alignment, at the end of the day they need to be able to support the delivery of new products and initiatives, ensuring the team has everything it needs to ship them. To achieve this, a PM will prepare documentation outlining the problem that needs to be solved and documenting the scope of the solution, hold a kickoff meeting to ensure that people responsible for implementing the solution know what they need to know about the customer needs, the business goals, and any constraints impacting the solution, works with customer success, marketing, legal and other teams throughout the product development to get everyone’s sign off and launch the product.
5. Champion the team
Product managers are expected to lead without authority. To build successful products, they work hard to make sure everyone on the team is aligned with and working towards the same goal, feels empowered to do their best work, and has everything they need to succeed. Product managers are always there to answer questions, help the customer success team to resolve an issue, and unblock the engineering team if they run into any challenges. At the end of the day, everything is about people so taking care of the people is critical.
A product manager is a broad role that requires superior communication and listening skills, the ability to switch contexts a lot, and a determination to do what it takes to make the product and the company succeed.
Jackie Bavaro, the author of Cracking the PM Career & Cracking the PM Interview and former head of product at Asana, created this incredible diagram of PM skills.

What if…?
If you are a security professional, I hope you have learned something new. Well, even if you are like myself a PM, I am still hoping it has inspired you to think about your role on a deeper level. Whoever you are, I am sure at this point, you are wondering — “So what?” PMs sounds cool but what do they have to do with cybersecurity? We are not launching products so why would we care?”
I am glad you asked.
As I was observing the mechanics of the cybersecurity industry, I noticed that there is a strong focus on the tech side of security — firewalls, endpoint agents, cloud workload protection, code security, and similar.
If you have read any of my other articles (say, this one), you probably know that I am a big believer in people-centered security. However, any time I talk about it, many folks come back with the argument that “security is a technical discipline, and you can’t solve it by talking to people”. I admit that this argument is a strong one, and it made me think more about how cybersecurity is structured as an industry. I started drawing parallels with other fields like software development and then it dawned upon me — “Product Management!”.
What follows is pure speculation — I do not have the evidence to say this is how anything should work. After all — I am a product manager, not a security practitioner. Instead of trying to convince you that I am right, I would like to invite you to explore the following: what if there was a role in security doing what a PM is expected to do in software development.
Opportunities in cybersecurity leadership
Before you dismiss this as a heresy, let’s do some thinking together. In software development, a product is generally built by a close collaboration of at least three groups: engineers, designers, and product managers. For simplicity, let’s only talk about engineers and product managers.
Engineers and product managers have their objectives and their own, very distinct, career tracks. Engineers generally report to a head/VP/director of engineering, and people pursuing their career in engineering can choose to go into the engineering leadership and become heads/VPs/directors of engineering or to become domain experts and grow as individual contributors in their respective fields.
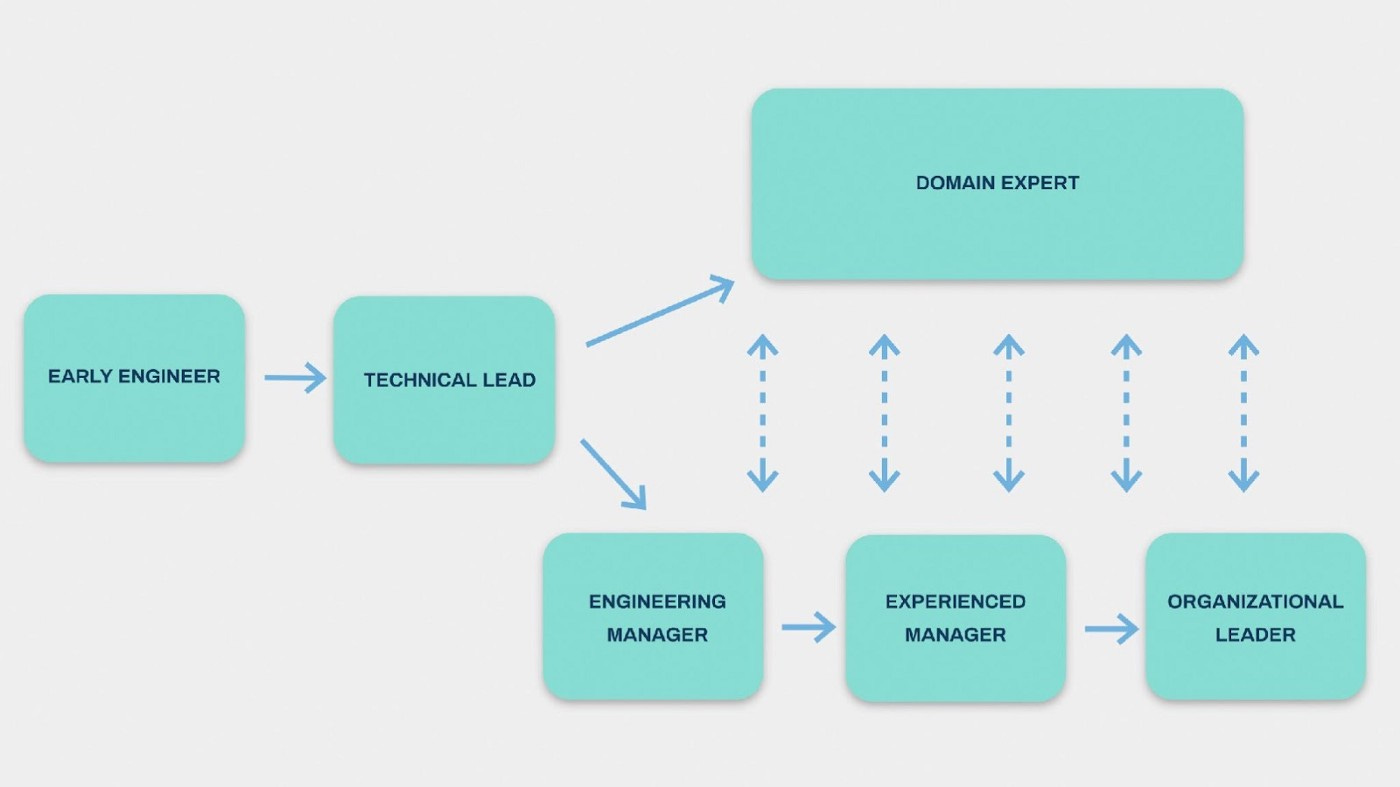

If we were to simplify the career focus, we can say that engineers are responsible for building products. It doesn’t capture the complexity of the role (nor is it intended to), but it makes our conversation more focused.
I would draw a parallel between software engineers and technical security professionals whose role is to identify vulnerabilities, implement cybersecurity controls, assess risks, and stay on top of the fast-changing security technologies. Similarly, some security professionals choose to specialize or grow their careers in security as individual contributors while others move on to eventually become CISOs (Chief Information Security Officers) or take similar roles.
What is incredibly important for our exercise is the fact that software engineers don’t decide what products to build. There are, of course, engineering initiatives that are decided and fully scoped by engineers, but when it comes to product work, it’s the job of product managers to make decisions about what the team will work on, and prioritize this work.
Imagine if there was an outwardly-facing, PM-like role on security teams designed for generalists who would be doing what a PM does — talking to people across the company, understanding their problems, translating these problems into security requirements for technical teams, championing security across different functional groups and ensuring that security team is at all times focused on the highest-value work. Let’s call this role a Security Champion (for the purpose of this exercise, the name doesn’t really matter).
What would the Security Champion do?
Following the PM list of responsibilities, let’s speculate what the Security Champion could be doing. For simplicity and ease of comparison, I will use the same five categories, rephrased just slightly.
Discover what the business & the users need
Security discovery is a process of building an understanding of what people do, what tools they use, and in what ways they can make the organization vulnerable. This knowledge can be used to put in place security controls that reflect the unique needs of the environment, and that are feasible, user-friendly, and valuable.
Tasks for Security Champion could look like follows:
Develop an understanding of the business — understand the business model, revenue channels, supply chain, internal processes, relationships between different departments, tools, and similar across the organization
Proactively gather and process feedback from internal users across different groups (finance, sales, engineering, etc.) and external third parties (suppliers, partners, etc.) to learn about their experience with security
Coordinate user research about a specific security measure that is currently being discussed
Brainstorm and prototype a security solution that addresses the security needs while ensuring a good user experience for people who will be affected
Prioritize what to implement
Every organization is unique, and its main priority will be defined more by its environment than by what’s currently on the news. While there might be a new attack vector trending on the news, if the company employees share passwords via email and re-use the same credentials across different systems, it is likely more fruitful to focus on addressing that problem first.
To prioritize what security measures to implement, a Security Champion would:
Look for actionable insights from the industry and monitor what’s happening in the security field, what trends are emerging, what organizations are being targeted and in what ways, etc.
Work with technical security and company leadership to establish a broad security strategy
Prioritize the most strategically valuable security initiatives
Meet with people from different departments (sales, customer success, finance, engineering, marketing, etc.) to evaluate the viability of planned initiatives and to ensure that they would not unreasonably impede the work of the people which would make them develop insecure workarounds
Discuss with technical security professionals to understand the amount of effort required to implement these measures and assess the feasibility
Create a prioritized backlog of security initiatives
Rally the team around security
The decisions of the security team impact everyone in the company. Most importantly, security is key to business continuity; if the organization cannot safeguard itself from attacks, it can suffer significant financial and reputation losses and be forced out of business. This is why a Security Champion would be expected to evangelize the importance of security across the company and explain what the organization is doing in the area of security and why. To get everyone aligned, a Security Champion may:
Deliver presentations on weekly all-hands to ensure that everyone on the team understands what security measures are being implemented, the rationale behind them, as well as their importance
Conduct regular sessions with people from different functional groups across the organization to ensure that they are aware of the security initiatives being worked on, how these initiatives will impact the day-to-day of the employees, and ensure a full buy-in around the security initiatives in question. Security teams have to become trusted partners and advisors on security, known for being helpful and having users’ interests in mind; if this doesn’t happen and people continue to be afraid of security teams, it will be hard to instill the right environment for security to thrive. Passing policies and sending emails is not how you can achieve a sustained change in the organization; for that, you need to build relationships and put people first.
Host a call with suppliers and partners advocating for mutually beneficial security measures and initiatives.
Deliver the security initiative
Once something has been prioritized for the technical security team to work on, the Security Champion would work with the team to implement the initiative. Implementation tasks could include the following:
Write a specification outlining the problem the security initiative is expected to solve, the proposed solution, and other requirements for the technical implementation.
Work with security architects and security engineers to prototype the solution that shows how the solution is going to work
Work with the team to identify and address gaps and edge cases not covered by the initial solution design
Work with legal and compliance to ensure that the solution as designed meets company compliance, privacy, legal and other requirements
Work with leaders from other departments to ensure they have everything they need to succeed once the new initiative is live
Monitor KPIs and metrics to ensure that security teams are focusing on the right problems and to track how the organization’s security posture is affected by the launched initiatives
Champion the team
Security teams today are understaffed and overextended. A Security Champion could work with the technical security team to ensure they all feel empowered and motivated to do the work, they have a strong sense of ownership over the outcomes, and their accomplishments are recognized. In the field where people feel constantly under pressure to outsmart and outpersist attackers, having someone who would champion the team is critical.
Some of the tasks could include:
Supporting employees from other departments when they have security-related questions and need one point of contact on the security team
Work with the support team to resolve issues related to access, privacy and security
Remove blockers for the technical security team by talking to CISO about a technical obstacle that is affecting the work of the team or is skiing them down
Where to find Security Champions
When I talk about the Security Champion, I imagine this person to play a double-sided role as both the advocate for employees’ needs on the security team and the evangelist of cybersecurity across the organization. Cybersecurity will unlikely become more human-centered without there being an advocate that security folks can have access to anytime they contemplate a new solution. At the same time, organizations will unlikely become more security-conscious unless there is someone passionately championing cybersecurity and building bridges between security & other departments.
Who would be ideal for this role? Generalists. They could be security professionals who enjoy cross-functional, people-centered work but don’t want to become people managers (note: on software development teams, engineers do not report to PMs). Or, they could be people with liberal arts degrees with a strong passion for security and the ability to become translators between technical and non-technical audiences.
It is easy to see that as security is getting more complex, we will need technical experts deeply specialized in their respective fields and focused on technology. At the same time, as organizations evolve and security becomes more and more important for business survival, we will also need people to connect the dots across different stakeholder groups, while championing cybersecurity.
These two tasks require people with radically different skill sets. We can, of course, try to push even more work on already overextended CISOs, but it’s likely better to do it differently. Software development has solved the problem by splitting the “what” & the “how” between two independent roles: engineers and product managers. Cybersecurity could follow the same path.
What about CISO?
CISOs today live under a lot of pressure. There are simply too many tasks on their plate for them to succeed: hiring, technology, vendor negotiations, security strategy, working with the board & executive leadership team, people and security leadership, and much more. Based on what I have been hearing — too much for them to succeed at everything. They could benefit from an employee on a team (or even a counterpart), focused on what I described above.
Let’s look at software development & try drawing the parallels with cybersecurity.
By focusing on “how” instead of both “how” and “what”, engineering leaders (directors, CTOs, VPs of technology, etc.) are able to dedicate the required amount of time to technical strategy, build empowered teams, grow their people, keep the leadership updated about what the team is working on, and more. The head of product (director/Chief Product Officer VP, etc.) is in turn taking care of the strategic direction of the product. This division does not imply that engineering leaders are not responsible for strategy — they are, it’s just the scope of that strategy is much more manageable when it is shared with product leaders.
Closing Words
I am a product leader, not a security professional. I have not worked on the security team, and by no means I do not possess what is needed to advocate for how security teams should be structured (nor am I looking to get in that place).
One thing I do know is that we need human- and business-centered professionals in the field. We need people who will bridge the increasingly complex technical side of cybersecurity with the problems, habits, and needs of people who are affecting and will be affected by security. We need people who understand the business goals and objectives as well as cybersecurity to prioritize the work technical teams are doing and to focus on what truly matters. We need people who would not use jargon or abbreviations when talking to the users, people who would talk in terms of simple to understand use cases, and who would be asking powerful questions instead of talking. We need security professionals armed with empathy and curiosity, not policies and procedures. We need people who will become experts in continuous discovery, a security-focused version of Teresa Torres’ work. We need people in security who see their work as being partners, not judges, people who can act like business enablers, not business warriors.
In software development, product managers are the ones who act as translators between business and technology. I don’t know what they will be called in cybersecurity — Security Champions, Security Owners, or whatever else will fit the bill. We need someone.




