Game of Thrones in cybersecurity: data gravity, industry consolidation, platform play, private equity, and the great cyber gold rush
One of my longest and most comprehensive deep dives into the future of cybersecurity to date. This piece attempts to define the industry outlook for the next 5-10 years.
Welcome to Venture in Security! Before we begin, do me a favor and make sure you hit the “Subscribe” button. Subscriptions let me know that you care and keep me motivated to write more. Thanks folks!
When you hear of Game of Thrones in the context of cybersecurity, what first comes to mind is the HBO hack of 2020 when the script of the TV series was allegedly stolen by malicious actors. It is not what this piece will be about. Instead, I will be discussing the complexities, intricacies, and strategies different players of the market employ as they fight for the ability to shape the future of cybersecurity.
This piece does not focus on 2023 and instead attempts to define the industry outlook for the next five to ten years.
Image Source: Unsplash
Embracing the inherent complexity of tracking cybersecurity market moves
Many factors impede our ability to understand where cybersecurity is going; I have previously talked about them in different articles, most notably Investing in cybersecurity: a deep look at the challenges, opportunities, and tools for cyber-focused VCs.
In the context of our discussion, I would like to zoom in on three factors.
1. Cybersecurity is a horizontal, not a vertical
I have not explicitly called out this factor before but it is critical for this conversation: unlike many other industries, cybersecurity is not a vertical but a horizontal. When you think about food delivery, human resources technology, payroll, mortgages, or any other field, you see them existing as stand-alone, well-defined verticals. Cybersecurity is unique as it touches on everything across all the verticals, and it is at the core of each vertical's existence.
Unlike other fields that help our society run more efficiently such as payments infrastructure, cybersecurity is not a separate functionality everything needs to interact with. Instead, it is a fundamental part of what everything is. While one payment provider can be replaced with another, and in some cases, the product can be entirely detached from the compensation for using it, the same cannot be done to cybersecurity.
2. There is an intelligent, well-motivated driver of innovation
Another layer of complexity unique to cybersecurity is the fact that one of the most critical drivers of the innovation is the adversary - a conscious, intelligent, well-motivated individual or a group of individuals actively trying to find holes, gaps, and blind spots in both organizations (consumers of security) and cybersecurity products (providers of security). The closest analogy I can find would be an arms race in which two or more nations try to outcompete one another in securing a favorable military balance.
The above two factors are relevant to our discussion for a simple reason: they both contribute to the ever-growing number of vendors. Every time a new technology emerges, it needs to be secured. Every time a new industry vertical emerges - it introduces unique processes that need to be secured. Every time an adversary finds a new path to penetrate the organization’s environment, there needs to be a way to address that. No company, however innovative, strategic, and well-funded, can successfully anticipate all events it needs to prepare for and execute on that knowledge. This is why cybersecurity innovation is most commonly acquired, not built in-house.
3. Platform as a Holy Grail of cybersecurity founders
To start a cybersecurity company, smart founders look for real problems and a pressing need for solutions, as well as a unique wedge that would allow them to compete. However big the founder's ambitions may be, due to the limited resources, startups have to start small, commonly focusing on one high-value use case for a narrowly defined customer group. This is the only sensible approach a startup can take given their need to move fast and get the right performance metrics quickly so that it can raise the next round of funding and doesn’t run out of cash (assuming we are talking about a venture-backed startup). This is also what investors are inclined to finance - passionate professionals solving a narrow problem they know everything about.
A notable side effect of having many startups tackling singular, well-scoped problems is the emergence of thousands of so-called “point solutions”. With some exceptions, point solutions tend to be valued lower compared to platforms or marketplaces where customers can access many cybersecurity products in one place. Most investors realize that in the long-term, platform play can yield more impressive outcomes, but they also understand that the chances of it succeeding are incredibly low. On the other hand, a point solution that “makes X easier or more cost-effective” is less likely to be a home run, but it is also less likely to go under. Point solutions require less capital, and typically have a higher internal rate of return (IRR) as well as shorter paths to an exit, whereas platforms can take a decade or more to get to an IPO or an acquisition. This risk-adjusted conundrum of platform vs point solutions investing causes many headaches to cybersecurity VCs.
Cybersecurity at the macro level is hard to read as there are thousands of small vendors, and mini-consolidation events can be seen at different parts of the market all the time.
Today, most security companies are private. As of the time of writing (1 Jan 2023), there are 17 pure-play cybersecurity companies listed on the US stock exchange - a few considering the size of the US cybersecurity market. The number of public cybersecurity companies has been rapidly shrinking due to a growing number of acquisitions by cloud providers, large security enterprises, and private equity firms, as well as the economic downturn which prevented businesses from going public. In 2022, there was only one cybersecurity IPO - Zero Fox - which went public on Nasdaq via SPAC on August 4, 2022. Most point solutions' will get acquired early and have their technology integrated by larger players trying to assemble a security platform, or merged with bigger products trying to solve the same problem. For the foreseeable future, there will be a need for the most innovative, “best-of-breed” point solutions to plug into platforms, - something I will discuss in more detail in subsequent sections.
Security at the source: “data gravity”, data warehouses, and cloud providers
To be able to run thought experiments and think about the future of cybersecurity, it is critical to understand the concept of data gravity. The idea was first introduced in 2010 by Dave McCrory, a software engineer who observed that as more and more data is gathered in one place, it “builds mass”. That mass attracts services and applications, and the larger the amount of data, the greater its gravitational pull, meaning the more services and applications will be attracted to it and the more quickly that will happen.
Data gravity leads to the tectonic shift in cybersecurity: security data is moving to Snowflake, BigQuery, Microsoft Azure Data Warehouse, Amazon Redshift, and the like. As the amount of data increases in size, moving it around to various applications becomes hard and costly. Snowflake, Google, Amazon, and Microsoft understand their advantage incredibly well and are taking action to fully leverage it. As it relates to cybersecurity, they typically do it in the following ways:
By offering their own security services and applications, and
By establishing marketplaces and selling security services and applications from other providers.
Image Source: Google Cloud
In the next few years, data warehouses and cloud providers have the potential to grow into the largest distribution channel for cybersecurity. Security companies capable of getting their foot in the door and building partnerships can sell their offerings entirely through this channel. Field sales representatives for data lakes and cloud providers, equipped with marketing collateral and information about cybersecurity solutions, can upsell and cross-sell their existing customer base with little effort. Data warehouses and cloud providers track two metrics: ingestion and consumption, or to put it differently - getting the data in, and ensuring that customers use as many add-ons and services as possible, fully leveraging the capabilities of the platform. Selling cybersecurity on top of their core offerings can drive consumption, help sales reps to hit their quotas, and provide all sides with steady streams of revenue.
Image Source: Snowflake
Back in 2020, Gartner predicted that by 2024, two-thirds of businesses will implement a multi-cloud strategy to reduce vendor lock-in. This is another challenge that increases ambiguity about the future of cybersecurity. A large enterprise typically has two cloud providers: a primary, and a secondary. While critical applications cannot run across two platforms due to the high costs, redundancy offers benefits for price negotiations, and to the degree to which it is reasonable and cost-effective, helps combat vendor dependency. A company can also end up with a multi-cloud setup if one of the subsidiaries it acquires uses a cloud provider different from its own. We are unlikely to see uniform cloud infrastructure environments across enterprises, which creates additional complexity. As of today, there are approximately 15 detection and response startups trying to tackle this problem. The question of multi-cloud is particularly interesting in the context of discussed above channel arrangements, and the fact that two cloud providers could integrate with different security vendors, making it harder for customers to consolidate all security data in one place.
Another question is about the way these changes will impact the Security information and event management (SIEM) space. I have personally heard stories about cases when getting security logs for analysis from cloud storage into a SIEM platform outweighs the maximum amount the company would stand to lose if the issues are not remediated. Said differently, it can be more cost-effective to do nothing than to investigate a potential security issue - a conclusion that paints a dark picture for industry leaders. It becomes apparent that the high cost of moving the data around, coupled with the challenges of throughput and latency, will make security teams do the majority of their work in data warehouses and cloud providers where the data resides.
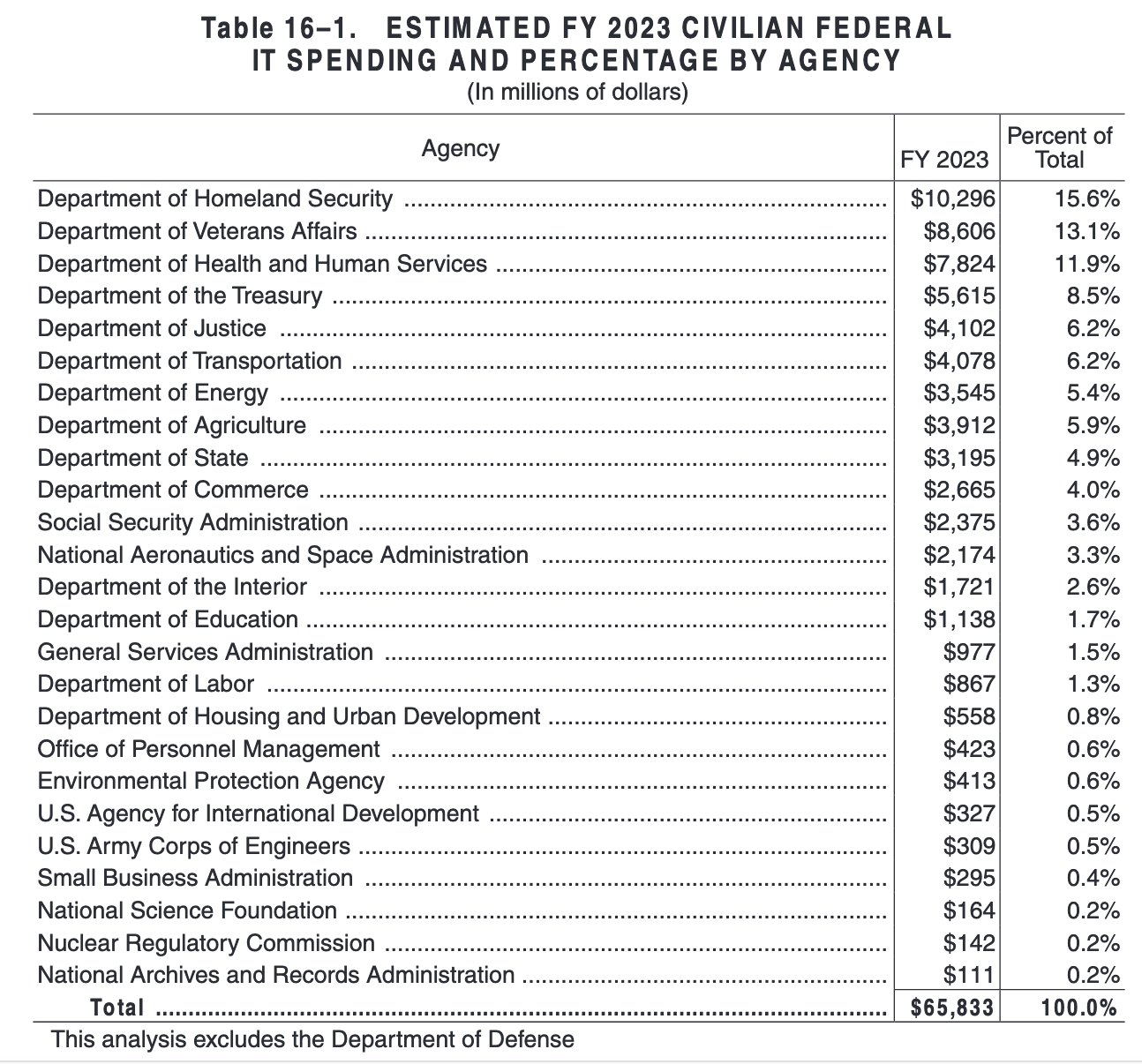
The battle for the future of the cloud and cybersecurity is intensifying in the public sector as well. At the end of 2022, the Department of Defense awarded Amazon, Google, Microsoft, and Oracle positions on the Joint Warfighting Cloud Capability contract worth potentially $9 billion over five and a half years. Cybersecurity is likely to be next in line. The 2023 President’s Budget allocated $65 billion for IT at civilian Federal agencies, and $10.9 billion specifically to support and upgrade Federal civilian cybersecurity capabilities. The total addressable market (TAM) is there, so we will be seeing increased competition for government spending.
Image Source: 2023 President’s Budget
Google: organizing the world’s [security] information
Google’s approach to security leverages its core competencies - big data, AI, and infinite scalability, offering companies to send their security data into the Google cloud ecosystem to achieve their desired outcomes. Google’s first notable security bet, Chronicle, did not become a big success, despite its radical promise of leveraging artificial intelligence and machine learning, supercharged with Alphabet’s treasure trove of security data, to help security teams protect their company’s networks. Stephen Gillett, then the CEO of Chronicle, had an ambitious goal: “We want to 10x the speed and impact of security teams’ work by making it much easier, faster, and more cost-effective for them to capture and analyze security signals that have previously been too difficult and expensive to find.”
Just over a year after the company’s public announcement, it unveiled Backstory which offered the ability to ingest and store large volumes of security data, with Chronicle's analytics engines continuously scanning it for threats. In 2019, Google reabsorbed Chronicle, the previously independent spinoff, back into its Google Cloud division. This merger has led to turbulent times for the security company, with some employees concluding that “Chronicle is dead, Stephen [Gillett] and Google killed it." Following the restructuring, the Chronicle’s CEO, chief security officer, chief technology officer, and several other key employees left. Now a part of Google Cloud, Chronicle continues to build new functionality, such as curated detections, managed by Google's threat intelligence team to reduce the amount of time and effort customers need to invest in designing their own coverage, announced in 2022.
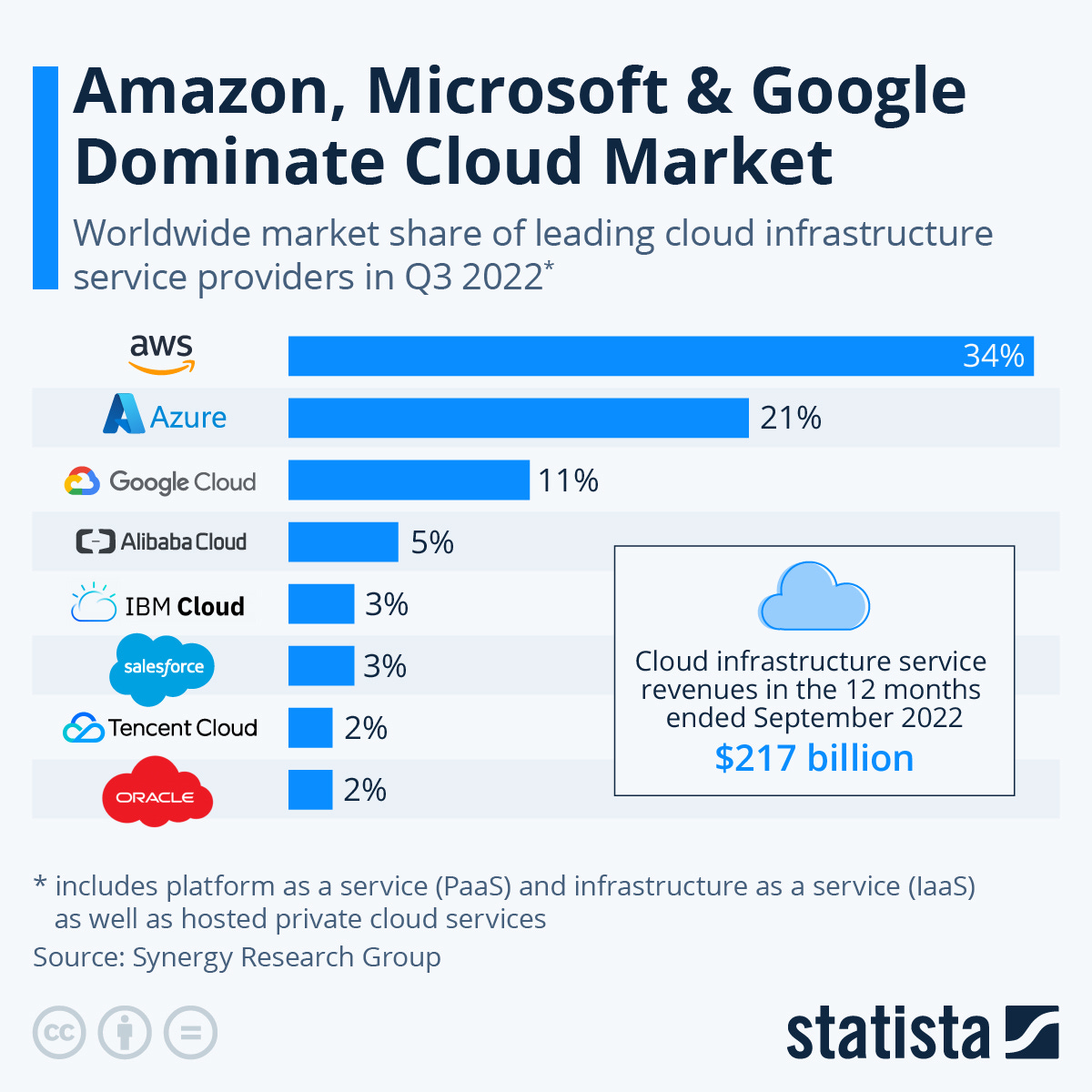
As Chronicle did not turn into a sweeping success, Alphabet needed to find a new way to try and establish itself as a serious player in cybersecurity, a task especially critical given that Google’s share of cloud services is far behind that of AWS and Microsoft.
Image Source: Statista
The year 2022 has been a pivotal year for Alphabet’s efforts to become a leading player in cybersecurity. To start, it launched several security offerings, namely a data loss prevention tool for BigQuery, followed by the software supply chain and zero trust security services. Most importantly, it completed two acquisitions: Siemplify, a leading security orchestration, automation, and response (SOAR) provider, and Mandiant, a leader in dynamic cyber defense, threat intelligence, and incident response services with strong ties to the federal government. Having built the tech stack to collect and analyze security telemetry at scale (Chronicle), and combined it with the ability to automate security operations (Siemplify), Google added 18 years of threat intelligence and incident response experience from Mandiant to the mix.
Alphabet has the capital, the team, and the motivation to become a leading force in cybersecurity. Even though it is lagging behind AWS and Microsoft today, it is moving fast to become a prominent player in the space.
Bundle cybersecurity in: a unique advantage of Microsoft
Microsoft Windows remains the dominant desktop OS globally with a share of roughly 76 percent as of 2022. This leadership position offers Microsoft a unique industry advantage - the ability to bundle cybersecurity with its other offerings. As Lytical Ventures wrote in its November 2022 Cyber Thoughts newsletter, “[Microsoft] is offering to bundle their endpoint solution, Defender, and offering free data upload to Sentinel from MS products along with customer licenses to Office 365 and the Windows OS. CIOs upgrading to MS E5 licenses are using the cost advantage of these by cutting the security tools that they replace to pay for the new licenses. This feels like the standard MS playbook of offering a product that is “good enough” and bundling it with the must-have products of the operating system and Office. Having said that, the Defender product is actually quite good, and CISOs are taking note.”
As with other bundles, it remains to be seen if security teams will want to use Microsoft offerings or if they will be looking for the “best-of-breed”, a trend that has been undercutting the ambitions of CrowdStrike, Palo Alto Networks, and other platform players. The pendulum between “best-of-breed” (point solutions) and “best-of-suite” (platforms) swings back and forth every few years, and now the “best-of-suite” seems to be winning with its promises of reducing the complexity, cutting the number of vendors, and lowering security spending. I have heard some anecdotal stories that CISOs have been losing the battle with their CIOs who are using the security cost-cutting to pay for Microsoft licenses. The argument goes as follows: "Removing Splunk can pay for the new Microsoft licenses". While some can continue to keep Splunk, keeping other EDRs when Defender “does the job” is a tough sell.
Microsoft’s ability to bundle cybersecurity into its offerings is supercharged by the company’s push to become vendor-agnostic. “Our goal is to help every organization strengthen its security capabilities through a Zero Trust architecture built on our comprehensive solutions that span identity, security, compliance, and device management across all clouds and platforms,” Microsoft’s CEO Satya Nadella said back in 2022. When we hear him speak about cross-cloud, cross-platform products, these are not empty statements as the company has indeed become more vendor-neutral. A case in point is Microsoft's identity offering - Microsoft Entra - which has been actively integrating with various third parties. Vendor neutrality appears to be one of the strategies enabling the giant to become more deeply interconnected with other players within the ecosystem and compete with companies such as CrowdStrike which many at Microsoft's security division see as a number one rival.
These strategic bets have been paying off: as of 2022, Microsoft has become the largest cybersecurity company with annual revenue of $15 billion and a strong ambition to grow from there.
The year 2022 has been very productive for Microsoft as well. In April, it brought together the former Azure Purview and the former Microsoft 365 Compliance portfolio under one brand - Microsoft Purview. In May, it announced the identity and access offering - Microsoft Entra - designed to serve as a unified admin center for Azure Active Directory, Entra Permissions Management, and Entra Verified ID, where an organization can verify and secure every identity or access request. In June, the company released Microsoft Defender for individuals, and in August it announced the general availability of Microsoft Defender Experts for Hunting “to support organizations and their cybersecurity employees with proactive threat hunting”.
Having acquired several cybersecurity companies before, in 2022 Microsoft’s M&A activity in the segment has been modest. It acquired Miburo, a cyber threat analysis and research company specializing in the detection of and response to foreign information operations. Contrary to the rumors that the company may buy Mandiant, the well-known cybersecurity research and incident response company was later acquired by Google instead.
Despite being a large company, Microsoft is capable of executing really well. Similar to Google, it has the ambition to go after the ever-growing security spending, but unlike Alphabet, it has more market share in the cloud and the advantage of being able to bundle the new products they build or acquire into existing company offerings.
Amazon: an everything store [for cybersecurity]
Amazon is the largest public cloud provider globally with Amazon Web Services (AWS) responsible for 34% of the market according to Statista. Unlike other cloud providers, such as the above-mentioned Google and Microsoft, Amazon does not share much about its security play. However, it does follow the same playbook that stems from the desire to leverage the data gravity effect. As noted by Matt Kapko, “AWS is acting as the central security advisor for its customers by choosing what to develop internally and selecting third-party vendors it deems best suited for tight integration with its platform.” Unlike Google and Microsoft, which have been more partner-friendly with their marketplace approach, Amazon prefers to cover all security needs of their customers without the heavy involvement of third-party solutions. While for now, they allow select partners to fill the gaps, Amazon is notorious for its ability to turn from a partner into a fierce competitor overnight by introducing its own products that compete with those of its partners.
At the 2022 AWS re:Inforce, the company announced a set of internal features and integrations that enable customers to access an ever-increasing set of cloud security services at scale, in one place. Later, at the AWS re:Invent, it unveiled Amazon Security Lake designed to automatically centralize security data from the cloud, on-premises, and custom sources into a purpose-built data lake stored in a customer’s account. Amazon Security Lake enables security teams to get a more complete understanding of their security data across the entire organization and improve the protection of their workloads, applications, and data. This announcement is yet another voice warning of the existential threat to the players in the so-called SIEM space.
Cybersecurity Dive rightly observed that Amazon’s quiet way of doing security is not an accident - the company is intentional in not trying to be perceived as a cybersecurity provider and focusing on the cloud instead, seeing security as a part of what they do. What complicates the ability to make definitive observations is the fact that Amazon does not share any numbers that would offer insight into the size of its security business. The AWS Marketplace offers over 4,000 integrations with security vendors and service providers, while Amazon’s own security offerings cover a wide variety of use cases, from managed threat detection to data protection and compliance.
Image Source: Amazon
Image Source: Amazon
Given that AWS is the leading cloud provider, it is very likely to be ahead of its rivals when it comes to cybersecurity - not simply because it started earlier, but because its attack surface is the largest so arguably they have to be. Having said that, Amazon to date has not positioned itself as a leading cybersecurity player - unlike Microsoft and Google eager to get their brands synonymous with security, the company has been quiet about its plans and its ecosystem play. As security becomes a differentiator and competition for the market intensifies, I expect Amazon will become more vocal about its role in the future of the industry.
Pure play cybersecurity enterprises: the gold rush
Acquire and integrate: Palo Alto's approach to building a security platform
Palo Alto Networks did a great job assembling a comprehensive cybersecurity platform to execute its go-to-market strategy of consolidation. The company’s value proposition is simple: do all of your security in one place, by replacing other point solutions and consolidating security spending. Palo Alto’s 2022 What’s Next in Cyber survey finds that 77% of security leaders are highly likely to reduce the number of security vendors and tools they rely on, and the company naturally wants to be the one that covers as many use cases as possible.
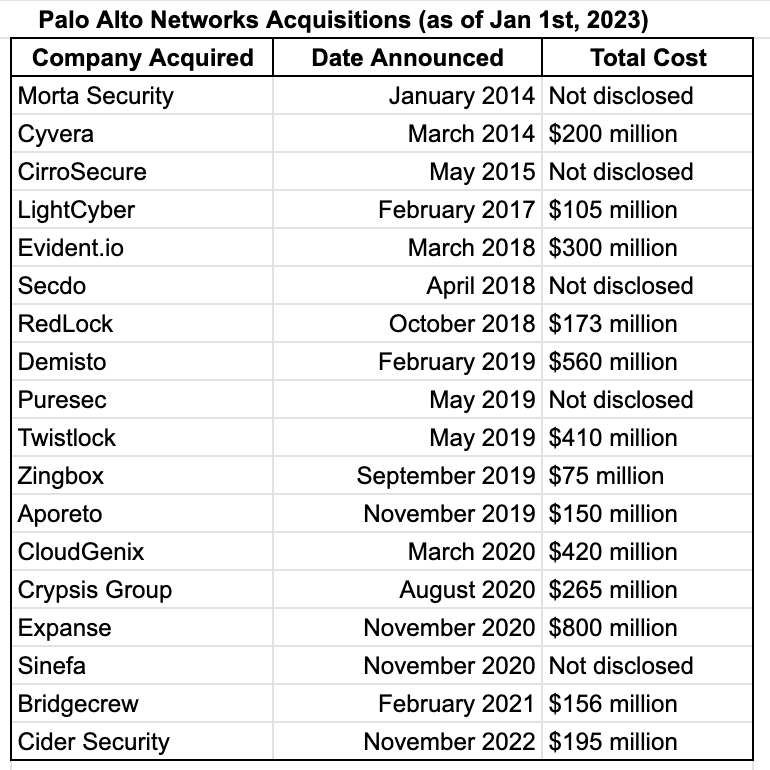
To deliver on its vision, Palo Alto needs a broad range of security capabilities, more than they can build in-house. To solve this problem, it has been pursuing a large number of acquisitions over the past few years, especially since 2018 when Nikesh Arora became the CEO. At the December 2022 Ignite event, Arora proudly stated that: “Across the board, we probably spent $4 billion on about 17 companies since I’ve been here. And I’d say most of them are working. Forty percent of companies are a net new capability that didn’t require integration, 60% require integration. And we had a common theme … to buy the No. 1 or two in the industry.”
Image Source: Internet Research & Palo Alto Networks
Palo Alto has been highly successful with this strategy, and Arora can take full credit for this success: it was largely under his leadership that the company expanded from firewalls into the broader security market. The company has a strong sales team and well-established channel partnerships, so for acquisitions, it does not seek a high annual recurring revenue (ARR) or an established customer base. Instead, it looks for innovative technologies that are in demand, solve real problems, and can be integrated with its Strata, Prisma Cloud, and Cortex platforms, leaving it to its sales channels to get them to the customers. Palo Alto’s sales force has mastered the art and science of upselling and cross-selling, and the company is aggressive about pursuing its expansion plans: while many companies were announcing layoffs in 2022, Palo Alto hired 550 new direct sales representatives - a clear sign that the company is looking to expand.
Palo Alto’s approach to building a security platform through acquisitions which have been a cornerstone of its success is also a liability with a strong potential to lead to future challenges. Trying to stitch a security platform by bringing together tens of separate companies is hard for multiple reasons. First, for many people who built startups being acquired, the acquisition is seen as an exit - the end of their journey. After the transaction completes, some choose to leave, and others have to stay, to, as it’s often called, “rest and vest”. Building a cohesive company culture and promoting innovation in this environment is not an easy task.
What’s even harder is creating an offering that can perform well at scale. Integrating a few external pieces into a platform designed from the ground up to work well with other components is challenging but possible. However, stitching tens of separate tools never designed to work with one another is a very tough task. Most of Palo Alto’s products are being assembled into its SaaS platform - Prisma. Although the company tries hard to integrate them into holistic offerings, there are gaps and many pieces work separately, not as one product, which results in inefficiencies, and challenges around latency and interoperability, to name a few. As the company buys more products not built to work together from day one, it will need to continue increasing investments in upgrading its infrastructure and tackling legacy issues and technical debt. That, in turn, will reduce the amount of capital Palo Alto can allocate to innovation and research and development, setting it behind on exploring emerging security needs, and as a result - leading to more acquisitions, thereby perpetuating the downward spiral.
For now, Palo Alto Networks is going strong, and its CEO recently made a statement that it “will be the first $100 billion cyber company".
The company is heavily invested to take advantage of the need to consolidate disconnected systems and tools, making this a cornerstone of their expansion strategy; they talked a lot about this strategy at Ignite ’22.
This is where the story gets interesting: on one hand, the previously described data gravity effect works against Palo Alto's desire to become the security juggernaut, but on the other hand, the need for companies to support hybrid and multi-cloud environments calls for a supercloud platform like what Palo Alto is trying to become. In the short term, the company is poised to grow, although it remains to be seen how optimistic its decade-long outlook will be.
Build from the ground-up: platform play of CrowdStrike and SentinelOne
CrowdStrike and SentinelOne are similar in many ways: they started around the same time, both are leaders in endpoint detection and response (EDR) and have now expanded into extended detection and response (XDR), and both are on the list of highly valued cybersecurity companies. Cole Grolmus of Strategy of Security has written a fantastic deep dive into both companies following their annual earnings recap (the article covers their performance until March 2022 but it remains highly relevant until today).
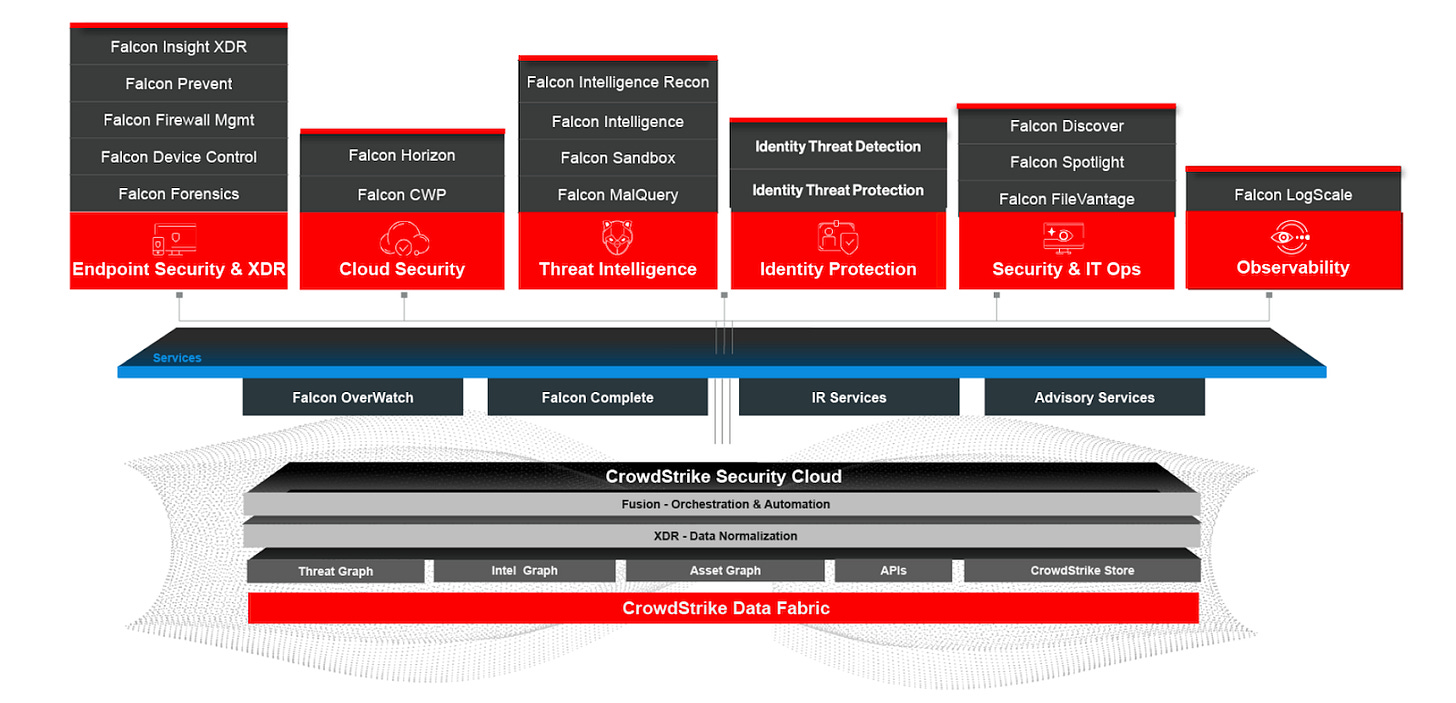
Like Palo Alto, CrowdStrike and SentinelOne have embraced a platform play seeing consolidation and focus on security tool reduction as the primary message in their go-to-market strategy. Both companies treat their extended detection and response (XDR) capability as a cornerstone for this consolidation, layering additional products and services on top. And, both players understand the threat coming from data warehouses and cloud providers quite well. CrowdStrike, for example, makes sure to emphasize that it is an “all-in-one” solution, and includes CrowdStrike Security Cloud/CrowdStrike Data Fabric.
Image Source: CrowdStrike
The word “platform” has been overused, especially in cybersecurity. Many companies offer tens of different modules, out of which only one or two see material usage, making them “platforms” by technical definition but “point solutions” according to the voice of the market. To clearly distinguish themselves from the wannabes, in its Q3 2022 earnings report, the company stated that “CrowdStrike’s subscription customers that have adopted five or more, six or more and seven or more modules was 60%, 36%, and 21%, respectively, as of October 31, 2022.”
CrowdStrike's platform play seems to mirror that of SentinelOne and vice versa: both companies have active marketplaces, namely the CrowdStrike Store and Singularity Marketplace. On top of that, both vendors maintain a presence at marketplaces of cloud providers: CrowdStrike lists offerings on both AWS and Google Cloud Platform, while SentinelOne is on AWS. At AWS re:Invent 2022, when Amazon announced the launch of its Security Lake, both CrowdStrike and SentinelOne went ahead with their announcements about integrating their data into the Amazon Security Lake.
As the extended detection and response (XDR) capabilities have become a commodity, and the competition in cybersecurity is intensifying, it is logical to expect CrowdStrike and SentinelOne to continue expanding their security capabilities. Product launches, partnerships, and acquisitions are not the only ways the two companies grow their presence in the ecosystem. In September 2022, SentinelOne launched S Ventures - a $100M fund to invest in enterprise cybersecurity startups. CrowdStrike has been investing in early-stage ventures since 2019 (I have previously written a deep dive on this topic - Corporate venture capital and cybersecurity: why Okta, CrowdStrike, CyberArk, and others invest in cybersecurity startups).
Just like Palo Alto Networks, both CrowdStrike and SentinelOne are forced to deal with the challenge of seeing security leaders look for the “best-of-breed” point solutions instead of adopting the integrated modules offered by security platform providers. Unlike Palo Alto which assembled its Prisma cloud from acquisitions, CrowdStrike and SentinelOne have built the vast majority of their modules in-house, designing them to work with one another from the ground up. As smaller players compared to Palo Alto, CrowdSrike, and SentinelOne have to be smart in the way they manage their expansion. CrowdStrike, in particular, has had an impressive track record over the past few years, so they do not want to make any acquisitions with the potential to reverse or even slightly impact their growth metrics.
Acquire, integrate, and reinvent: Thoma Bravo and private equity role in reshaping security
Before looking at some of the effects private equity (PE) firms have had on cybersecurity, it’s worth briefly covering how PR works. While some private equity firms follow the so-called “buy, strip and flip” path, the strategy that has been known to yield significant returns is one known as “buy and build”, best explained by David W. McCombie III of Forbes: “Most private equity funds capitalize upon this last factor by acquiring several smaller companies at one valuation multiple and then reselling the packaged group at a higher valuation multiple, often described as a “buy and build strategy.” This results in a natural food chain as companies consolidate: Small lower middle-market funds start with an initial ‘platform’ business that has sufficient scale and a good organizational foundation to absorb additional add-on (or bolt-on) acquisitions, along with some organic growth initiatives. Eventually, the fund will sell this bigger company to a larger middle-market fund which will then pursue a similar strategy aggregating and (sometimes) integrating similar assets that are packaged with the intent of selling to an even larger fund. This process continues as the asset gets continually larger and eventually ends with an acquisition by a large (often public) company or an IPO (less common nowadays).”
Private equity firms active in the cybersecurity space, such as Thoma Bravo and Vista Equity Partners, tend to take this exact “buy and build” approach: acquiring platform security companies and then assembling a broad range of point solutions to become a part of these platforms. This gives PE players the ability to access more customers, and upsell and cross-sell to their existing customer base, thus increasing the Average Contract Value (ACV) - an approach similar to that of Palo Alto. What’s different about private equity is that unlike large security giants such as Palo Alto, their model is typically more near-term: buy the company, take it private, achieve large operational efficiency, grow sales, and sell it to the buyer willing to pay the most. Private equity firms typically do not hold onto their portfolio companies for decades.
Thoma Bravo has been the most impactful PE player in the cybersecurity space - both in terms of the size of its security portfolio, as well as the amount of money it is willing to pay (take their $12.3 billion purchase of Proofpoint in 2021 as an example). The company’s portfolio lists 27 security vendors. It does not yet include ForgeRock acquired in October 2022 as the transaction is expected to close in early 2023.
Image Source: Thoma Bravo
Thoma Bravo appears to be taking an interesting approach to portfolio construction by acquiring companies in segments critical to the security infrastructure of the future and building the ecosystem around them. In the past year, the firm has assembled a large portfolio in one specific sub-segment of the market - identity and access management commonly referred to as IAM. Identity is a fast-growing market, and a unique one as it covers two sub-segments traditionally served by different security vendors: internal (employees) and external (vendors, partners, and customers). While there are many IAM providers on the market such as Microsoft, Okta, OneLogin, and Ping Identity, among others, a large customer would typically work with one of the three - Okta, Ping Identity, or ForgeRock. Two of the three - Ping Identity and ForgeRock - are now a part of the Thoma Bravo portfolio.
In April 2022, Thoma Bravo paid $6.9 billion for SailPoint, in August it acquired Ping Identity for $2.8 billion, and in October it announced the acquisition of ForgeRock. Earlier in 2020, the firm made a strategic growth investment in Venafi, a machine identity management provider. And, to top it off, the company also owns a minority stake at Delinea, formerly known as Centrify. These moves have led to the consolidation of the identity space, now largely divided between Thoma Bravo and Okta which previously acquired auth0.
It is hard to say what Thoma Bravo is planning to do with the identity providers it assembled as the company does not share a lot. Chip Virnig, a Partner at Thoma Bravo, highlighted during the announcement of ForgeRock purchase that “identity-centric cybersecurity solutions are a critical enabler for businesses to digitally transform their operations”. We know that ForgeRock is well positioned to serve the largest enterprises with unique needs and many layers of complexity, and Ping Identity is a large, established provider with a strong reputation and solid customer base. It’s possible that Thoma Bravo will be trying to stitch all three products together into an all-in-one identity platform, and that it will be using identity, the critical component of company security, as a cornerstone of the platform strategy. Following the variation of the data gravity approach, the company can use identity as a cornerstone of the sales channel for other product categories from its portfolio.
It is clear that while the cybersecurity space as a whole is too broad and too chaotic to confidently talk about industry consolidation, we are indeed seeing the consolidation of the identity management segment.
Cyber as a matter of national security
The Game of Thrones described in this piece is happening in parallel with rising alarms about the need to protect critical infrastructure, safeguard trade secrets, and other matters of national security that require attention at the highest levels of the government, going well beyond what the market can do on its own.
As noted before, the government’s cybersecurity spending is growing, and with that - its dual role as a regulator and a customer. As a regulator, the government is there to oversee the market behavior, and ensure fair competition. As a customer, it needs the ability to acquire cybersecurity capabilities at scale, streamline its purchasing process and get the ability to partner with a small number of pre-vetted, trusted, and highly reliable security vendors. In this duality of the government’s interests lies the dilemma: will it take the path of limiting the industry consolidation by citing fair competition and anti-monopolistic clauses, or will it give a green light to large leaders such as cloud providers to do what needs to be done to strengthen national security? It remains to be seen what happens. We have not seen many cases when the regulator would block the process of industry consolidation so far, which in my opinion is an early indicator that the government could be rightfully prioritizing the matters of strengthening national security.
When it comes to the government as a customer, it tends to seek ways to enter into large service delivery contracts with platform companies. The public buyer is looking for one-stop shops instead of manually assembling the “best-of-breed” capabilities from multiple providers. Today, the federal cybersecurity budget is split by large players like Palo Alto, as well as some startups who were able to break through the complex public acquisitions process, such as Tanium and Axonius. In the coming years, I anticipate we will be seeing the consolidation of government security spending, and a shortlist of “all-in-one” providers will be awarded the biggest contracts.
Putting it all together: looking at the future of cybersecurity
We often hear analysts and industry insiders talk about the consolidation of cybersecurity. While that is surely happening in some segments of the market such as IAM, the reality and the broader context at the macro level are much more complex.
The dynamics of the cybersecurity industry are fascinating to observe. We see several large companies such as CrowdStrike, SentinelOne, and Palo Alto Networks trying to outcompete one another with their consolidation-focused “all-in-one” platform strategies, Microsoft dominating the market by leveraging its leadership in the PC space, cloud providers leveraging data gravity to offer security, and private equity firms amassing huge cybersecurity portfolios. All this along with other moves and trends I touched on in this piece are just the tip of the iceberg. There is more - the changing role of integrators and resellers, and the increased investment in cybersecurity from venture funds, corporations, and family offices, to name a few. Add the ever-rising number of cyber threats and concerns at the highest levels of the government about matters of national security into the mix, and you will realize that it is not easy to deduce even the short-term direction of the market, let alone predict the long-term trends.
The future of cybersecurity is being built now. Some trends are already quite visible, such as the maturation of the industry and the move from promise-based to evidence-based security, or the rising importance of security engineers. Others, such as the formation of cybersecurity platforms, are at earlier stages.
Looking into the future, I see data gravity as a defining trend that will shape the direction of cybersecurity. I think a decade from now, a lot of what we see today as the cybersecurity market will get absorbed by the leading cloud providers, and I think we are seeing Amazon, Microsoft, and Google steadily assembling the capabilities to do this. Matthew Prince, CEO of Cloudflare, in his interview with Protocol, puts it best: “I remember pretty clearly when Bill Gates said [in the future] "there will be no anti-spam companies.” Everyone in the space laughed at him. But he was just dead-right. What he saw, that others didn't see, was that if you have enough data, and you're running it all through systems that you control, you can solve a lot of these problems very effectively. For traditional spam, Gmail and Microsoft and others have largely solved the problem. If you try today to run your own mail server, it's really difficult. But because everything is consolidated behind a relatively small set of email providers, they have largely tackled the spam problem.”
The cloud providers, however, won’t be able to eliminate all problems. The talent shortage, the cost of hiring security professionals, and the deep expertise required will make it impossible for every company to have a security team. This is where I believe service providers will come in - not as resellers of security tools, but as trusted security advisors able to help small and medium companies, as well as the ever-growing number of self-employed individuals, to secure their data. Mature enterprises with unique environments and a lot at stake, on the other hand, will continue needing specialized security expertise and will be forced to embrace evidence-based security. Security vendors, I think, will be solving more advanced problems not covered by the “spam filters of the future”. Tools built in a modular way from the ground up will find their place in that new market, while those assembled by bringing together tens of widgets not designed to talk to one another, will slowly fade away.
Some areas such as endpoint security will continue to be a problem but we are seeing large parts of it also move to the cloud. Google’s Chrome OS, and recently - Microsoft’s Windows 365 which takes the operating system to the Microsoft Cloud are good examples of this shift.
While all this combined can give an idea of the direction I think the market is going in, the level of ambiguity is high. Even if things unfold the way I described, which itself is probabilistic, it would just be a small piece of what we would see. We are many years from being able to call security a solved problem, so the need for innovative approaches is as strong as ever.
In the short term, for the next five or so years, I think we will start seeing marketplaces run by cloud providers become more and more important as distribution channels for security products and services. No matter the approach of the parent company, be it developer-focused like that of Amazon, enterprise-focused like that of Microsoft, or mixed like that of Google, I think their importance will continue to grow. So is the importance of multi-cloud and vendor-agnostic solutions willing to open their ecosystems to third parties to contribute and integrate with.
In coming years, the competition in the industry will intensify, driven largely by the cybersecurity gold rush - the growing number of cyber breaches, and the desire of founders and investors to capitalize on the opportunity. As always, those who succeed in their ambition to build platforms will be generously rewarded, and those who identify opportunities and quickly address them with point solutions will continue to be paid off in smaller ways, but with higher levels of confidence.
For now, the number of tools enterprises need to rely on is growing, the number of security attacks and attack vectors is growing, and the battle for industry domination continues. And with that, the Game of Thrones in cybersecurity goes on.
Acknowledgements
Making sense of the industry trends at a macro level is hard. This deep dive would not have been possible without the privilege to get perspectives and feedback from, run thought experiments, and debate ideas with Chris Behrens of SYN Ventures, Andrew Smyth of Atlantic Bridge, Ernie Bio of Forgepoint Capital, and Lucas Nelson of Lytical Partners. The idea to title this piece the “Game of Thrones'' came from the conversation with Eric McAlpine of Momentum Cyber. As always, all opinions and conclusions are my own.









Hi Ross, thanks for the great insight! Curious to know where do you think Fortinet sits in this landscape?
Great articles on cybersecurity! Do you think Palo Alto's firewall business could get disrupted in the future, with the move to the cloud or with more companies taking a SASE approach?